
Perdagangan Opsyen Binari selalunya dikelirukan dengan perdagangan Forex. Dagangan Opsyen Binari tidak sekuat perdagangan forex. Ia melibatkan meletakkan pertaruhan pada pasaran tertentu sekejap. Artikel ini akan membincangkan lebih lanjut tentang peniaga Pilihan Perduaan dan bagaimana warga Bahrain boleh memulakan perdagangan pilihan binari dalam pasaran kewangan hari ini.
4 broker terbaik untuk berdagang dengan di Bahrain:
Lihat 5 broker Pilihan Perduaan terbaik di Bahrain:
100+ Pasaran
- Menerima pelanggan antarabangsa
- Bayaran tinggi 95%+
- Platform profesional
- Deposit cepat
- Perdagangan Sosial
- Bonus percuma
100+ Pasaran
- Min. deposit $10
- tunjuk cara $10,000
- Platform profesional
- Keuntungan tinggi sehingga 95%
- Pengeluaran cepat
- Isyarat
300+ Pasaran
- Deposit minimum $10
- Akaun demo percuma
- Pulangan tinggi sehingga 100% (sekiranya ramalan yang betul)
- Platform ini mudah digunakan
- Sokongan 24/7
100+ Pasaran
- Platform profesional
- Akaun demo percuma
- Deposit minimum $10
- Webinar dan pendidikan
- Bayaran yang tinggi
100+ Pasaran
- Menerima pelanggan antarabangsa
- Bayaran tinggi 95%+
- Platform profesional
- Deposit cepat
- Perdagangan Sosial
- Bonus percuma
daripada $50
(Amaran risiko: Dagangan adalah berisiko)
100+ Pasaran
- Min. deposit $10
- tunjuk cara $10,000
- Platform profesional
- Keuntungan tinggi sehingga 95%
- Pengeluaran cepat
- Isyarat
daripada $10
(Amaran risiko: Dagangan adalah berisiko)
300+ Pasaran
- Deposit minimum $10
- Akaun demo percuma
- Pulangan tinggi sehingga 100% (sekiranya ramalan yang betul)
- Platform ini mudah digunakan
- Sokongan 24/7
daripada $10
(Amaran risiko: Modal anda mungkin berisiko)
100+ Pasaran
- Platform profesional
- Akaun demo percuma
- Deposit minimum $10
- Webinar dan pendidikan
- Bayaran yang tinggi
daripada $10
(Amaran risiko: Dagangan adalah berisiko)
Apa yang anda akan baca dalam Post ini
Senarai 4 broker Binari terbaik di Bahrain
Secara umumnya, terdapat banyak yang sesuai broker binari seluruh dunia. Dengan begitu banyak pilihan, sukar untuk menyimpan gambaran keseluruhan. Oleh itu, kami telah memilih yang terbaik untuk anda. Jadi, mari kita ketahui lebih lanjut tentang broker binari terbaik di Bahrain.
#1. Quotex
Jika anda ingin mula berdagang pada Quotex, anda perlu membiayai akaun anda dengan sekurang-kurangnya $10. Platform broker membolehkan pedagang untuk berdagang dengan serendah $1. Quotex adalah salah satu yang terbaru dan broker yang paling dipercayai yang wujud hari ini. Pejabat pertama syarikat adalah di United Kingdom. Broker itu mula beroperasi pada 2019, tetapi ia sudah mempunyai lebih 600,000 pedagang di seluruh dunia.
Quotex mempunyai a akaun demo untuk peniaga. Akaun demo sangat mirip dengan akaun sebenar. Jadi ia adalah latihan yang betul yang anda perlukan sebelum anda mula berdagang dengan akaun sebenar anda.
The platform tersedia pada telefon sebagai aplikasi. Anda juga boleh berdagang pada desktop anda. Kedua-dua peranti mempunyai ciri yang serupa di dalamnya.
Mengenai Quotex:
- Deposit minimum: $10
- Aset: Indeks, Tenaga, Forex, Kripto
- Platform termasuk: Apl mudah alih dan Web
- Sokongan: 24 jam – sehari
- Leverage: 1:500
- Bonus: Tiada
Adakah Quotex sah di Bahrain?
Ya, perdagangan pilihan binari pada Quotex dibenarkan sepenuhnya di Bahrain. Kekurangan semasa garis panduan peraturan khusus untuk perdagangan pilihan binari dalam talian di Bahrain tidak menjadikannya haram. Pedagang dari Bahrain dengan yakin boleh menggunakan semua ciri dan perkhidmatan yang ditawarkan oleh platform dagangan dalam talian yang boleh dipercayai ini tanpa kebimbangan undang-undang.
(Amaran risiko: Modal anda boleh berisiko)
#2. IQ Option
Syarikat pembrokeran popular untuk berurusan dalam kedua-dua Pilihan Perduaan dan Forex. Ibu pejabat di Cyprus dibina pada 2013 untuk menyediakan perkhidmatan kewangan kepada pedagang Eropah dan pedagang lain di seluruh dunia. IQ Option terkenal kerana menyediakan pelbagai aset untuk perdagangan Opsyen Binari.
Broker juga menyediakan ceramah untuk peniaga di platformnya. Kuliah ini membantu mereka untuk mengetahui lebih lanjut tentang perdagangan Binari. Anda mesti mendepositkan jumlah minimum $10 untuk memulakan dagangan pada IQ Option. Peniaga boleh menggunakan aplikasi mudah alih dan platform web untuk menjalankan transaksi.
Platform broker diketahui mempunyai salah satu daripada antara muka yang paling interaktif. IQ Option mempunyai platform ciptaannya sendiri yang membantu pengalaman dagangan pelanggannya.
Mengenai IQ Option :
- Deposit minimum: $10
- Aset: Saham, ETF, Forex, Kripto
- Platform: Apl mudah alih
- Sokongan: perkhidmatan 24/7
- Leverage: 1:500
- Bonus: Tiada
Adakah IQ Option sah di Bahrain?
Pedagang di Bahrain boleh menggunakan perkhidmatan IQ Option secara sah sebagai platform dagangan pilihan binari. IQ Option menawarkan pelanggannya platform dagangan tersendiri untuk berdagang pelbagai aset popular. Pada masa ini, ketiadaan peraturan khusus untuk perdagangan pilihan binari dalam talian di Bahrain tidak menjadikannya sebagai aktiviti yang menyalahi undang-undang.
(Amaran risiko: Modal anda boleh berisiko)
#3. Pocket Option
Deposit minimum untuk memulakan dagangan pada Pocket Option bermula dari $50. Selepas deposit ini dibuat, anda boleh mula meletakkan dagangan dengan mana-mana aset yang tersedia pada platformnya. Tempat yang dipanggil Kepulauan Marshall telah menjadi rumah kepada broker Pilihan Perduaan ini sejak 2017.

Peniaga Pocket Options mempunyai akaun demo, sama seperti akaun sebenar. Ini membolehkan pelanggannya merasai platform sebelum mereka mula berdagang pada akaun langsung mereka. Jika anda biasa dengan platform MT4, yang ini menggunakan platform MT5 memberikan pedagang pengalaman dan ciri yang lebih baik untuk dinikmati.
Pocket Option mempunyai a aplikasi mudah alih yang boleh dimuat turun dari kedai mainan google atau App store anda. Anda juga boleh berdagang di desktop anda di tapak web broker.
Mengenai Pocket Option:
- Deposit minimum: $50
- Aset: Mata Wang, CFD, komoditi, Saham
- Platform: MT5
- Sokongan: 24/7
- Leverage: 1:100
- Bonus: Selamat datang, pulangan tunai dan kod promosi
Adakah Pocket Option sah di Bahrain?
Pocket Option ialah firma perdagangan undang-undang terkemuka yang beroperasi di Bahrain dan semakin popular kerana perkhidmatannya yang berkualiti tinggi di kalangan pedagang tempatan. Pada masa ini, tiada peraturan eksplisit yang mengkategorikan perdagangan pilihan binari dalam talian di Bahrain sebagai haram.
(Amaran risiko: Modal anda boleh berisiko)
#4. Olymp Trade
Lama dalam perniagaan penyediaan perkhidmatan Binary Options kepada peniaga, Olymp Trade ialah platform broker Pilihan Perduaan yang terkenal. Terima kasih kepada betapa bagusnya platform itu, ramai pedagang dari negara di seluruh dunia berdagang pada Olymp Trade.
Olymp Trade menyediakan aset yang mencukupi yang boleh digunakan oleh pelanggan untuk memilih pasaran mereka dan mula membuat keuntungan. Untuk mula meletakkan perdagangan, anda perlu terlebih dahulu deposit minimum $10 ke dalam profil anda. Anda boleh menavigasi platform dengan mudah kerana teknologinya yang dipertingkatkan dan pantas.
Anda boleh berdagang pada anda telefon atau komputer. Peniaga Olymp Trade juga mendapat maklumat tentang keadaan pasaran. Maklumat ini berfungsi sebagai gambaran tentang pergerakan pasaran untuk peniaga.
Mengenai Olymp Trade:
- Deposit minimum: $10
- Aset: Emas, OTC, CFD.
- Platform tersedia: MetaTrader 4, Olymp Trade
- Sokongan: Perkhidmatan 24 jam setiap hari
- Leverage: 1:500
- Bonus: Tiada
Adakah Olymp Trade sah di Bahrain?
Pada masa ini, kekurangan peraturan rasmi yang mengawal perdagangan pilihan binari dalam talian di Bahrain tidak menjadikannya haram. Adalah penting untuk ambil perhatian bahawa Olymp Trade ialah broker pilihan binari yang sah yang beroperasi secara sah di Bahrain.
(Amaran risiko: Modal anda boleh berisiko)
Bagaimana untuk Mendaftar untuk Pilihan Perduaan di Bahrain
Mendaftar tidak menjadi masalah. Proses ini sangat mudah untuk seseorang kerana ia boleh dilakukan dari rumah atau pejabat anda atau zon selesa anda hanya melalui skrin anda. Proses pendaftaran bermula seperti ini:
Pertama, anda perlu mempunyai akaun e-mel untuk membuka akaun anda. Sebaik sahaja anda mempunyai permohonan broker atau mendaftar di laman web, anda akan meletakkan e-mel ini dan kata laluan yang dikehendaki. Kedua-duanya akan digunakan untuk membuat akaun anda terlebih dahulu.

Selepas ini telah dilakukan, anda perlu mengesahkan alamat mel anda pernah mendaftar. Sebaik sahaja anda mengesahkan bahawa ia adalah milik anda daripada mel yang dihantar kepada anda oleh broker, anda kemudian boleh meneruskan semula ke platform untuk melengkapkan proses pendaftaran anda.
(Amaran risiko: Modal anda boleh berisiko)
Langkah seterusnya adalah untuk anda mengemukakan beberapa dokumen. Dokumen ini membantu mengesahkan identiti anda sebagai pedagang sebenar dari Bahrain. Anda akan menyediakan a alat pengenalan diri dan bukti pemastautin. Sebaik sahaja anda menangkap dan menyerahkan dokumen ini, anda perlu menunggu selama 24 jam sebelum anda boleh mengakses platform dan mula berdagang dengan akaun sebenar anda.
Jika, selepas 24 jam, akaun anda belum dibuat, anda harus menyerahkan semula dokumen atau menyemak mel anda untuk melihat sama ada terdapat sebarang mel daripada syarikat pembrokeran yang memberi anda maklumat tentang cara menyelesaikan isu tersebut.
Adakah Pilihan Perduaan sah di Bahrain?
ya, ia adalah sah untuk berdagang Pilihan Perduaan di Bahrain. Bahrain, walau bagaimanapun, tidak mempunyai mana-mana badan peraturan atau kawal selia yang mengawal Pilihan Perduaan di negara ini.

Negara, bagaimanapun, menggalakkan individu untuk mengambil bahagian di dalamnya. Kerana tiada peraturan yang mengawal Pilihan Perduaan di Bahrain, ramai orang menganggap bahawa ia adalah perdagangan haram. Ini tidak begitu. Pastikan anda berdagang di platform broker yang mempunyai lesen pengawalseliaan antarabangsa.
Peraturan Kewangan di Bahrain
Peraturan kewangan di negara ini telah dipindahkan dari satu badan ke badan yang lain. Sebelum mencipta CBB, yang bermaksud Bank Pusat Bahrain, organisasi yang dikenali sebagai Agensi Kewangan Bahrain itu bertanggungjawab ke atas sektor kewangan di negara itu.

Hari ini, CCB bertanggungjawab untuk mengawal selia institusi kewangan yang berada di negara ini. Bank Pusat ini juga bertanggungjawab mengagihkan wang dalam negara. Semua institusi kewangan, termasuk bank perdagangan, mesti dilesenkan oleh CCB sebelum dianggap sebagai entiti undang-undang.
(Amaran risiko: Modal anda boleh berisiko)
Perdagangan Opsyen Binari tidak mempunyai sesiapa yang mengawasinya. Inilah sebabnya mengapa pedagang Bahrain harus berdagang dengan broker asing yang dikawal selia oleh organisasi kewangan antarabangsa.
Bagaimana untuk Deposit Dana untuk perdagangan Pilihan Perduaan
Selepas mendaftar, akaun anda mestilah telah disahkan dan sedia untuk digunakan. Kamu perlu membiayai akaun anda sebelum anda boleh mula berdagang di atasnya. Membiayai akaun anda agak mudah. Cari butang pada skrin peranti anda yang telah didepositkan padanya. Sebaik sahaja anda mengklik padanya, anda akan diberikan kaedah pembayaran yang berbeza untuk membiayai akaun anda.
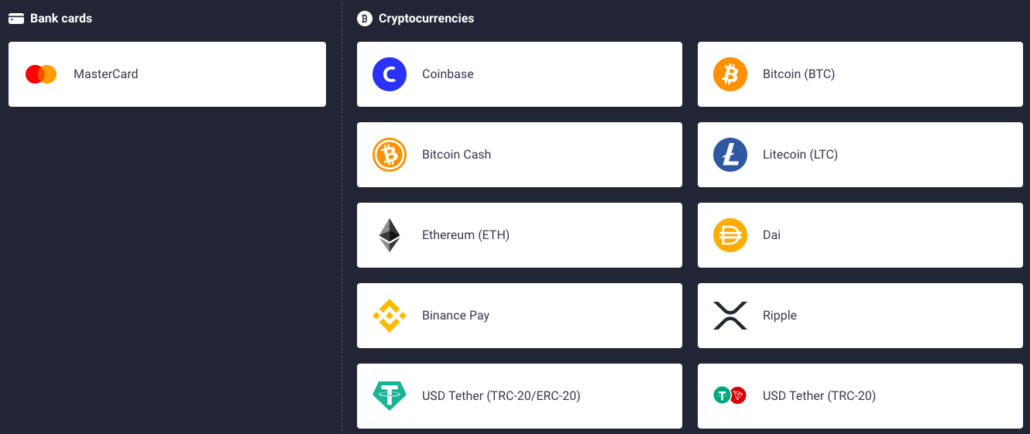
Pilih kaedah pembayaran yang mudah untuk anda. Kaedah pembayaran boleh melalui transaksi bank terus. Bermakna wang itu akan diambil dari akaun anda tanpa kad. Proses ini biasanya mengambil masa. Selain daripada transaksi bank langsung, anda boleh memilih penggunaan kad Mastercard atau Visa untuk membiayai akaun anda.
(Amaran risiko: Modal anda boleh berisiko)
Ambil perhatian jumlah paling sedikit yang boleh anda deposit ke dalam akaun anda pada platform broker. Ia berbeza-beza, jadi pastikan anda jangan cuba deposit wang kurang daripada deposit minimum pada platform broker. Semak di atas untuk deposit minimum broker yang berbeza.

Cara Menarik Diri
Mengeluarkan dana hampir serupa dengan mendepositkan dana ke dalam akaun anda. Untuk mengeluarkan wang anda, anda perlu pilih kaedah pembayaran juga. Ini boleh dalam pelbagai cara. Untuk satu, anda boleh memilih pilihan wang masuk ke akaun bank anda. Atau anda boleh memutuskan bahawa anda menginginkannya dalam dompet elektronik yang anda miliki. Sesetengah platform broker mungkin mengenakan bayaran kepada anda untuk pengeluaran. Jumlah yang kecil.

Satu perkara yang baik ialah anda boleh mengeluarkan wang daripada platform broker ini pada sebarang peranti yang anda gunakan. Adakah anda menggunakan aplikasi mudah alih? Anda boleh membuat pengeluaran. Adakah anda menggunakan desktop? Anda juga boleh membuat pengeluaran dengan mudah.
(Amaran risiko: Modal anda boleh berisiko)
Biasanya, percubaan untuk mengeluarkan dana anda terus ke dalam akaun bank anda akan mengambil sedikit masa. Jadi anda perlu bersabar dengan ini. Masa kelewatan bergantung pada platform broker, bank yang anda gunakan dan kestabilan rangkaian.

Bagaimana untuk Berdagang Pilihan Perduaan
Kami akhirnya datang untuk bercakap tentang bagaimana anda boleh mula berdagang Pilihan Perduaan sebagai peniaga di Bahrain. Untuk memulakan perdagangan Opsyen Binari, terdapat beberapa langkah yang perlu anda ikuti. Pilihan binari mudah difahami. Penjelasan langkah demi langkah di bawah ini akan membantu anda memahami dengan lebih baik.

Langkah-langkah yang perlu diambil semasa berdagang Pilihan Perduaan termasuk yang berikut.
Langkah #1: Menonton arah aliran pasaran
Pasaran adalah tidak pernah tetap dalam perdagangan Opsyen Binari. Sentiasa ada kenaikan atau penurunan harga aset yang anda gunakan untuk berdagang. Menonton trend pasaran akan membantu anda untuk menentukan bagaimana pasaran berubah setiap hari.

Menonton arah aliran pasaran memerlukan teliti belajar. Pasaran Pilihan Perduaan bergerak dengan sangat pantas. Inilah sebabnya mengapa ia memerlukan perhatian penuh anda apabila menontonnya. Menontonnya akan menjadi penentu langkah seterusnya yang perlu diambil.
(Amaran risiko: Modal anda boleh berisiko)
Langkah #2: Pemilihan pasaran
Pemilihan pasaran dilakukan dalam dua cara. Ia melibatkan memilih pasaran yang paling memihak kepada anda.
- Dagangan jangka masa

Apakah masa terbaik untuk anda berdagang? Orang ramai mempunyai masa yang berbeza mereka memilih untuk berdagang. Ada yang berdagang setiap hari, ada yang setiap empat hari, ada yang setiap minggu. Dagangan jangka masa membantu anda mengetahui masa pasaran paling menguntungkan.
- Minat anda
Kadang-kadang anda minat boleh mempengaruhi pilihan pasaran anda. Anda mungkin lebih suka pasaran tertentu kerana aset pasaran. Aset ini mungkin mata wang. Mungkin anda lebih suka berdagang dengan mata wang tertentu.
Langkah #3: Menarik tempat dan menetapkan masa tutup
Ini melibatkan anda memilih kedudukan dan pukul berapa anda mahu dagangan berakhir.

Ia serupa dengan ramalan dalam pertaruhan. Antara masa ini dan itu, pasaran akan jatuh di bawah mata anda atau lebih tinggi daripada mata anda.
Langkah #4: Tempatkan perdagangan
Selepas memukul tempat dan menetapkan masa tutup, anda perlu mengesahkan perdagangan.

Apabila anda mengesahkan, perkara seterusnya yang perlu anda lakukan ialah memerhatikan bagaimana perdagangan berjalan.
Langkah #5: Tamatkan dagangan anda atau anda tunggu sehingga tamat
Langkah terakhir ini akan menentukan sama ada anda mempunyai a untung atau rugi. Jika pada penghujung masa yang anda pilih, anda tidak mencapai pertaruhan, maka anda akan mengalami kerugian. Jika anda berpendapat bahawa situasi tidak akan memihak kepada anda sebelum dagangan anda ditutup, maka anda harus menamatkannya.

Tetapi jika ia berjalan lancar, maka anda boleh menunggu untuk tamat.
Kebaikan dan keburukan perdagangan Opsyen Binari di Bahrain
Perdagangan pilihan binari di Bahrain adalah pedang yang memotong di kedua belah pihak. Ia mempunyai kelebihan dan kekurangan. Semak mereka!
Kelebihan Dagangan Binari ialah:
- Anda mempunyai kawalan penuh ke atas wang yang anda risiko melalui dagangan kerana anda bebas memilih jumlah untuk berdagang dan cara untuk meletakkan dagangan anda.
- Dagangan adalah dalam talian; oleh itu tidak perlu memuat turun dan memasang perisian dagangan.
- Jangkakan perdagangan yang mudah pada setiap masa, tanpa mengira tempat dan masa.
- Anda tidak perlu mengambil risiko melainkan anda pasti, terima kasih kepada akaun demo yang tersedia.
- Broker tidak mengenakan sebarang bayaran tersembunyi.
Keburukan Perdagangan Binari ialah:
- Perdagangan pilihan binari hanya mempunyai dua pilihan, semuanya atau tiada, justeru berisiko.
- Walaupun seseorang boleh kalah atau menang, kerugian biasanya lebih tinggi daripada ganjaran kerana ia bermakna kehilangan semua pelaburan anda jika anda kalah.
Risiko Dagangan Pilihan Perduaan di Bahrain
Pilihan binari perdagangan mempunyai beberapa risiko, termasuk:
- Anda berdagang dengan rumah tanpa kawalan ke atas aset asas, dan selalu benar bahawa rumah itu menang pada penghujung hari.
- Sesetengah peniaga mungkin tidak tahu bila untuk mengambil tempat duduk belakang dan dengan itu terus bermain walaupun kalah, dan itu berakhir dengan teruk.
- Perdagangan pilihan binari terdedah kepada penipuan dengan banyak penipuan dalam industri; oleh itu mungkin kehilangan pelaburan anda walaupun sebelum anda berdagang atau selepas membuat keuntungan.
Bahrain adalah sebuah negara pulau kecil yang terletak di Teluk Parsi di Timur Tengah. Negara-negara yang terletak berhampiran Bahrain ialah:
- Arab Saudi: Bahrain berkongsi satu-satunya sempadan daratnya dengan Arab Saudi. Tambak Raja Fahd menghubungkan Bahrain dan Arab Saudi, memudahkan pengangkutan darat antara kedua-dua negara.
- Qatar: Bahrain terletak agak dekat dengan Qatar, dengan kedua-dua negara dipisahkan oleh perairan Teluk Parsi. Terdapat sambungan feri dan udara tetap antara Bahrain dan Qatar.
- Kuwait: Walaupun Bahrain tidak berkongsi sempadan darat langsung dengan Kuwait, ia terletak berdekatan dengan Kuwait merentasi Teluk Parsi.
Negara berhampiran Bahrain

Bahrain adalah sebuah negara pulau kecil yang terletak di Parsi Teluk di Timur Tengah. Jika anda tinggal atau bekerja di mana-mana negara ini, anda mungkin berminat dengan maklumat mengenai perdagangan pilihan binari di negara ini juga. Ikuti pautan di bawah untuk menerima maklumat daripada kami.
Ini adalah negara-negara yang terletak berhampiran Bahrain:
(Amaran Risiko: Modal anda boleh berisiko.)
Kesimpulan: Perdagangan Opsyen Binari boleh didapati di Bahrain
Membuat wang tambahan tidak semestinya sukar, terima kasih kepada perdagangan pilihan binari di Bahrain. Walau bagaimanapun, jika anda menganggap proses itu sukar, itu jauh dari kebenaran. Panduan di atas menunjukkan bagaimana perdagangan pilihan binari adalah berjalan-jalan di taman.
Ia juga haram; maka tidak perlu risau dengan pihak berkuasa. Apa yang anda perlu lakukan ialah memilih broker dagangan yang tidak akan mengecewakan anda. Contoh yang sangat baik ialah Quotex, Pocket Option, Olymp Trade dan IQ Option.
Soalan Lazim (Soalan Lazim) tentang Pilihan Perduaan di Bahrain:
Adakah berdagang Pilihan Perduaan di Bahrain cara yang ideal untuk membuat wang?
Ya, adalah mungkin untuk membuat keuntungan besar melalui pilihan binari perdagangan di Bahrain. Lakukan analisis pasaran yang betul, letakkan perdagangan, dan tunggu hasilnya.
Broker mana yang sesuai untuk berdagang Pilihan Perduaan di Bahrain?
Senarainya panjang, tetapi ada yang lebih baik daripada yang lain, menjadikan dagangan mudah untuk anda mengaut keuntungan. Ia termasuk Quotex, Pocket Option, Olymp Trade dan IQ Option.
Adakah perdagangan binari sah di Bahrain?
Ya, anda tidak akan melanggar mana-mana undang-undang dengan berdagang pilihan binari di Bahrain. Walau bagaimanapun, tidak semua broker dagangan adalah sah oleh itu keperluan untuk memilih dengan bijak.
Berapa banyak wang yang anda perlukan di Bahrain untuk berdagang pilihan binari?
Perdagangan pilihan binari di Bahrain selalunya memerlukan deposit permulaan antara $10 hingga $250, bergantung kepada broker yang dipilih. Walau bagaimanapun, adalah penting untuk mengenali risiko besar yang berkaitan dengan bentuk perdagangan ini dan untuk melabur hanya dana yang anda mampu dengan selesa untuk kehilangannya.
Apakah kaedah pembayaran biasa untuk broker pilihan binari di Bahrain?
Pedagang yang berpangkalan di Bahrain kerap menggunakan kaedah pembayaran seperti kad kredit MasterCard dan Visa, pemindahan bank dalam talian dan dompet digital.
Apakah risiko pilihan perdagangan binari di Bahrain?
Perdagangan pilihan binari di Bahrain penuh dengan risiko tinggi kerana ketiadaan peraturan dan sifat spekulatifnya, yang meningkatkan kemungkinan penipuan dan penipuan. Kesederhanaan pilihan binari yang jelas boleh menutupi bahaya ini, meletakkan peniaga pada risiko besar kehilangan pelaburan mereka.
Bolehkah anda berdagang pilihan binari secara percuma di Bahrain?
Ya, anda mempunyai pilihan untuk menggunakan akaun demo yang disediakan oleh broker, membolehkan anda melibatkan diri dalam perdagangan pilihan binari tanpa perlu menggunakan atau melabur sebarang wang.








