- Broker
- Fees
- Deposit
- Withdrawal

RoboForex review – Should you sign up or not? – Broker test
- Regulated by the IFSC
- Fast order execution
- 8 asset classes
- Leverage up to 1:2000
- Free demo account
- Spreads from 0.1 pips
Profitability in forex trading partly depends on the online broker you use. The internet is full of many online brokers claiming to be the best. A few charge reasonable fees and offer exceptional services that help traders succeed in the game. It is not the case for others. The only way to know if a broker is right for you is by using its services.
That is why we have gone ahead to test various online brokerage services. The review below focuses on one of the famous brokers, RoboForex. We will give you detailed information about the company’s offerings, platforms, fees, and other necessary facts. If you are searching for a suitable broker to invest in the financial markets, ensuring your objectives align with the broker’s profile is an important consideration. Read on to find out whether RoboForex will be right for you or not.

What is RoboForex? – Quick facts about the company

RoboForex is a global online brokerage company that originated in Belize. The broker came into being in 2009 and accepts traders from 169 countries. Many consider the broker a trusted and reliable partner in financial market investments.
RoboForex provides access to invest in various markets, including stocks, forex, indices, ETFs, energy, groceries, metals, and commodities.
Over 3.5 million active customers have accounts with them across the world. The broker has branch offices in the United Kingdom, New Zealand, and Cyprus. RoboForex is internationally recognized and has won several awards for its exceptional service. The company currently holds the Global Forex Awards for the Best Mobile Trading App and the Most Trusted Broker (2022).

Facts about RoboForex:
- Founded in 2009
- Global offices in the Asia Pacific, Europe, and the UK
- Award-winning Mobile Trading App
- Over 3.5 million active customers
- Provides access to famous assets
- Annual revenue over $74 million
Regulations – Is RoboForex regulated?

RoboForex has its home base in Belize and operates with a license from the International Financial Service Commission IFSC (Belize). This entity operates under Belize’s Ministry of Securities and Financial Service Commission Act.
The IFSC oversees the activities of brokers and financial institutions holding its license. They ensure strict compliance with customer protection laws and fair practices.

The broker is also a member of the International Financial Commission. This body is responsible for resolving financial disputes between brokers and traders. As a member of the commission, RoboForex participates in its Compensation Fund. The scheme provides up to €20,000 insurance for customers who deal with brokers.
The broker’s license numbers:
- International Financial Service Commission, IFDS: No. 000138/437
These licenses and memberships show that the broker is legit and can be trusted to deliver quality service. The regulators require transparency and fair dealings. Therefore, they carry out regular checks to ensure the broker continues to operate within the standard policies.
Security measures for traders and your money

RoboForex holds licenses from two acclaimed financial entities that ensure customers’ money is separated from the brokers to keep it safe.
These bodies also require strict adherence to data protection laws. Therefore, their licensees must use encryption and other necessary data protection programs on their web portals and platforms. Customers’ details and other information are well hidden from online hackers and data thieves as a result.
A good broker allows customers to focus on trading and investing by guaranteeing the security of funds and data. RoboForex shows its seriousness in this regard by going a step further to obtain membership with the Financial Commission.

The commission ensures its members contribute to a compensation fund that must provide settlement of up to €20000 if the need arises. So in the event of a financial claim that the broker can not handle, the commission must step in to ensure the customer gets compensated.
RoboForex also offers Negative Balance Protection, a feature that keeps market volatility from driving an account balance into a minus. Not many reputable brokers can provide such a service.
These security measures are in place to give customers a sense of safety and a worry-free trading experience. The company guarantees the safety of customers’ funds and data while dealing with them.
Review of the offers and RoboForex trading conditions
Customers can access more than 12,000 markets and eight asset classes on RoboForex’s platforms. These assets include the most popular and profitable ones in the financial market. We introduce these asset offerings below:
Stocks

Over 50 popular company stocks and numerous CFDs are available to trade and invest in. These include the most popular global brands, such as Netflix, Google, Microsoft, eBay, Tesla, Apple, and many more. Spreads on this asset on average are 2 pips, which falls within the market average fees. During active hours, popular stocks can fluctuate between 2 pips and 3 pips spreads. But this also depends on the account type. We discuss this further below. Customers can also access leverage of 20:1, and zero swap charges for non-leverage trades.
Stock trading is available on its five account types, but the RStock Trader is specifically designed for this purpose. Floating spreads can drop to 0.1 pips.
| Stock assets: | 50+ |
| Leverage: | Up to 1:20 |
| Spreads: | Usually between 2 & 3 pips |
| Execution: | Instant |
| Availability: | During stock exchange opening hours |
Forex pairs

RoboForex offers 40+ currency pairs to trade on any of its accounts. All its account types allow access to the forex markets, including popular major, minor, and exotic pairs like EURUSD, GBPUSD, USDNZD, USDJPY, etc.
Leverage of up to 1:2000 is provided, though it depends on regulations in your region. The fees on trading forex vary according to account type. Commission fees apply to the ECN and Prime accounts. But the minimum spread is 0.1 pips. The Standard and Cent account is zero-commission types, with floating spreads starting from 1.0 pips.
| Currency pairs: | 40+ |
| Leverage: | Up to 1:2000 |
| Spreads: | From 0.1 pips |
| Execution: | Instant |
| Availability: | During trading hours |
Indices

Indices are famous among investors because of their low-risk, high-liquidity nature. RoboForex allows you to access profitable ones, including Dow Jones, Nasdaq, SPX, and more.
A minimum deposit of $10 on RoboForex gives access to trade these markets at competitive fees. Depending on the account type, the average spread to expect is 0.5 pips. A $4 commission fee applies to a volume of $ 1 million trade. But this depends on the account too.
| Indices: | 27+ |
| Leverage: | Up to 1:500 |
| Spreads: | 0.5 pips on average |
| Execution: | Instant |
| Availability: | During trading hours |
ETFs

Like indices, ETFs are also popular because it lets you trade a group of company shares as a single stock. So you can diversify your investment at reduced trading costs. The minimum deposit to trade ETF on RoboForex is $100, higher than the Standard account minimum deposit.
But the spreads can drop to zero, and there are more than 1000 ETFs to choose from, including commodity ones. Leverage of up to 1:20 is available if you require it. The commission charge is $0.0045 per share.
| ETFs: | 1000+ |
| Leverage: | Up to 1:20 |
| Commission charge: | $0.0045 per share |
| Execution: | Instant |
| Availability: | During trading hours |
Commodities

Soft commodities are in high demand in the financial market, making them a liquid and profitable portfolio set to consider. RoboForex allows customers to trade and invest in cocoa, wheat, sugar, fruit, corn, coffee, and soybean on its RStocksTrader.
Spreads start from 0.1 pips, and the minimum deposit is $100 to trade. Leverage is available on request, and customers can get up to 1:20 to trade. There are no swap charges on zero leverage positions.
| Commodities: | More than 100 ETFs on soft commodity markets |
| Leverage: | Up to 1:20 |
| Spreads: | From 0.06 pips |
| Execution: | Instant |
| Availability: | Stock exchange opening hours |
Metals

Metals, such as gold are great investment options for hedging your funds against inflation. That means you can protect your capital from losing value due to rising living costs.
With a $10 minimum deposit, RoboForex lets you trade or invest in its several metal offerings, including gold, silver, platinum, palladium, and more.
Metals are available on all account types and platforms. The minimum floating spread is 0.0 pips. Except on the cent and pro accounts in which spreads start from 1.3 pips.
| Metals: | More than 20 ETFs on platinum, palladium, copper or nickel |
| Leverage: | Up to 1:1000 |
| Spreads: | From 1.3 pips |
| Execution: | Instant |
| Availability: | Stock exchange opening hours |
Energies

Through its MetaTrader 4 and RStocksTrader, RoboForex provides access to the energy commodity markets. With at least a $10 deposit, you can trade and invest in popular oil brands, including Brent and WTI. Other natural gases, ethanol, and more energy commodities are available.
You can also access various markets on this asset class through the broker’s CFD offerings. Spreads start from 0.0 pips, depending on the account type.
| Energies: | 100+ |
| Leverage: | Up to 1:100 |
| Spreads: | From 0.0 pips (depending on account type) |
| Execution: | Instant |
| Availability: | Stock exchange opening hours |
Cryptocurrencies (CFDs)

Over the years, RoboForex has increased its cryptocurrency CFD asset offerings from four to thirty-three. That means customers now have a selection of these markets to work with. Note that only 14 cryptocurrency CFD types are accessible on MetaTrader 4 and 5. But they include popular ones like Bitcoin, Litecoin, Stellar, Solana, Ethereum, Ripple, and others. The RTrader displays all 33 cryptocurrencies CFDs, including ETF and stock markets. The starting spreads on the ECN and Prime accounts are 0.07 pips. The RTrader offers tighter spreads starting from 0.0 pips.
| Cryptocurrency CFDs: | 33+ |
| Leverage: | Up to 1:50 |
| Spreads: | From 0.0 pips (depending on account type) |
| Execution: | Instant |
| Availability: | During trading hours |
Trading fees – How much does it cost to trade on RoboForex
RoboForex fees depend on the account type and the asset you trade. The broker uses floating spreads on its platforms of which the minimum ranges between 0.0 pips to 1.3 pips.
There are commission-based accounts, the ECN, Prime, and R-Trader, which attract commission fees, but with tighter spreads. During active market hours, traders can enjoy super tight spreads on them.
The Pro-cent and Pro-standard are non-commission-fee accounts. But spreads do not drop below 1.3 pips.
The lowest commission charge per trade is $4 for a round turn. Standard commission fees for a $ 1 million volume is $15. The fees all fall within competitive market rates.
Swap fees apply only on leverage positions above 1:1 and depend on the asset.
| Account type: | Trading cost: |
|---|---|
| Pro Cent | Spread floating from 1.3 pips |
| Pro Standard | Spread floating from 1.3 pips |
| ECN | Spread floating from 0 pips |
| Prime | Spread floating from 0 pips |
| R StocksTrader | Spread from 0.01 USD |
Test of the RoboForex trading platforms

RoboForex uses Straight-Through-Processing, known as STP execution methods for trading services on its standard accounts. ECN execution methods are employed for other account types, which give direct access to a vaster liquidity pool.
These execution methods are unlike dealing-desk kinds. They connect the customer to the liquidity providers where trades get matched with the best prices. The broker conducts these services on its selection of multiple platform offerings, including:
MetaTrader 4 and MetaTrader 5

These are popular in the industry because of their many trading indicators, charting, and other tools to help traders profit in the financial market. The MetaTrader 5 comes with the MetaTrader Market where traders can access various robots and indicators for successful trading. Demo versions allow you to test these tools before investing in them.
The broker’s MetaTrader platforms are downloadable on Android and iOS stores, making them compatible with mobile. RoboForex also offers a free VPS to customers once you signup and download the MT5.
RTrader

The RTrader is RoboForex’s proprietary platform and allows you to trade all the available markets. It’s charting and indicators are similar to MetaTraders and the cTrader. Stocks and ETFs are popular assets traded on this platform. The platform supports auto-trading and allows you to build trading robots, even without programming knowledge.
Social and copy trading is available through CopyFX. The service connects traders to a community of investors where you can access different tools, ideas, and strategies. They are said to offer among the best copy trading services.
Indicators & charting availability

RoboForex’s MetaTrader 4 and 5 offers more than 50 technical indicators, including the most useful ones like Moving averages, Bollinger bands, MACD, Ichimoku Kinko Hyo, and more. The RStocksTrader allows access to all the markets and provides in-depth technical analysis, market news, multiple charts, and more. A clear candlestick chart display helps you see crucial details at a glance, including opening price, highs, lows, and closing. These platforms include drawing tools, allowing you to construct trendlines to understand the market’s position.
In-built Expert Advisors, designed with the best indicators, are easily accessible. Traders can use the free creation kit on the RTrader to design and customize their own trading robots.
Mobile trading via the RoboForex app

Mobile trading has become essential to let users track their trades on the go. Many find it more convenient to trade on their smartphones than on a computer.
RoboForex’s platforms are all accessible on mobile phones. The MetaTrader 4, 5, cTrader, and RTrader are available on Apple iOS and Android. That means traders can access all instruments and essential tools to trade conveniently. You can also deposit and withdraw funds in mobile accounts. Social trading is available on mobile through the broker’s CopyFX feature. Basically, every function available on the desktop is also on the mobile apps.
RoboForex mobile trading offers:
- Same trading experience as the desktop
- Simple user interface for convenient trading
- News updates, analysis, and social trading functionalities
Tutorial on how to trade on the RoboForex platform

No matter what assets interest you, research and analysis should precede trading. Finding out the asset’s past price movements is key to successful trading decisions.
The knowledge will guide you in choosing the appropriate strategy for the market you wish to trade. Numerous strategies are available online, but not all apply to every market. That is why analysis is crucial to trading in the financial market.
Once you have done the necessary research, you can trade your desired asset. Log in and select the asset symbol in the quotes list. Type in the order details and set some risk measures through the limit orders. That means entering the position type (buy or sell), and lot size, setting the stop loss, then confirming these details. Place your trade once you are sure the details are accurate.
How to trade forex on RoboForex
RoboForex offers 40+ forex pairs on its platforms. That means not all the currencies are available to trade. So you should first check that your desired currency pairs are available to trade. Fortunately, most of the broker’s forex offerings are highly liquid and profitable.
Once you find your preferred forex assets, follow the steps below to trade:
Step 1: Market analysis

The typical analysis used in forex trading is technical analysis. It involves studying past price moves to predict future price direction. The various indicators and charts are of great benefit for this. They show all the price behaviors and potential moves in the forex charts. Although reading these charts requires some technical knowledge. Many traders who find technical analysis tedious often turn to Price Action for their market analysis. This method presents an easier approach and the necessary information to understand the price movements.
Step 2: Conduct tests on demo or cent account

The analysis would have given you enough information and helped you decide on a strategy. But it is not wise to trade with real money until you have tested your approach. RoboForex provides a free demo account for testing. The account comes with free credits to conduct many trades. If you desire real market tests, then the cent account is a great option. With as low as $10, you can enter the real forex market to test your styles and strategies before making a full commitment.
Step 3: Trade forex on a live account

After the tests come actual trading on your preferred live account. Once you log in, click on the currency pair you wish to trade. Choose your position based on the result of the analysis you conducted. At this point, you should employ some risk management to minimize your exposure. Stop-loss and take-profit are examples of the best ones for beginners and inexperienced traders.
Step 4: “Eyes on the Money”
You need to be watchful of the market while your position is open. Depending on the strategy, you would have to stay glued to the screen or check the trades regularly. That would help you adjust the order or exit the trade at the appropriate time. For this reason, people find mobile trading convenient and efficient.
How to trade Binary Options on RoboForex
Binary options trading is no longer available with the broker since 2016.
How to trade cryptocurrency CFDs on RoboForex

RoboForex offers up to 33 cryptocurrency CFD types from which to choose. Traders now have various choices to diversify their investments. Trading cryptocurrencies CFDs is the same on all its platforms, though you can access the complete list only on the RTrader.
Because these assets have higher volatility, a thorough analysis is crucial to trading and investing. It is a tricky market with frequent changes in price directions. The assets see a lot of highs and lows in prices within very short periods.
A good trading plan should follow a thorough analysis. That helps you set a target and maintain focus while your positions are open. It is easy to get jittery if the market starts moving against you. A trading plan and target help you stay on course. That way, you can hold out to watch the market move back in the direction that favors your position. A great approach is to close and exit once the price reaches your target. You can always open new trades to take advantage of the opportunities perceived.
As many have said, “trading is not for the faint of hearts.” The statement is truer with cryptocurrency CFD assets. Emotional management is vital to successfully trade them.
How to trade stocks on RoboForex

RoboForex gives access to stocks trading directly or through CFDs, indices, and ETFs. The first step to investing in stock is to determine how you wish to do it or the markets you prefer.
You can decide on this by studying the various markets and focusing on the most liquid ones. Business news reports and books on stock investments are a great start in this area.
Once you have decided on a market, the next step is to analyze the price movements. That would give you valuable insight into the asset and help you make the best forecasts while trading. Analyses lead to an approach, which means you can decide on the most suitable strategy only after conducting the right analysis.
Before placing trades on a real account, use the demo to test your approach. The demo is free and contains enough virtual funds for this purpose. It replicates the live market conditions. So if your trades yield a profit on it, it shows that your strategy will be profitable on the live account.
After the test, log in to the real account to trade. Select the asset symbol from the quotes list. Click on the new order and enter the necessary transaction details. Then place the trade, but don’t forget that limit orders are also applicable risk measures here. Trade only a few positions at a time for a start, until you build confidence and experience.
How to open your trading account

Setting up a trading account with RoboForex is straightforward. The first stage takes about a minute to complete. On the broker’s website, click on open account located on the top right side of the homepage.
Type in the initial required details to begin. Your full name, email, country, and phone are all that is necessary at this stage. After that, you will be redirected to a page where you choose between a demo or a real account.

A demo account is usually activated immediately. But a live account will require further details from you. Depending on your choice, the broker will send an email containing assigned details for the demo account or a link to confirm the registration.
The demo assigned details will include a username and password. With that, you can sign in and start trading on the broker’s demo. The link on the live account authenticates your email and lets you complete your registration. The complete form will contain options to choose your preferred account type and send them further personal details.
According to financial regulations, RoboForex will require a government-issued ID and address confirmation. So you will need to scan and upload a copy of your current utility bill or bank statement and the ID to the broker.
Once RoboForex receives and confirms these documents, the account creation will get processed within a few minutes to 48 hours. RoboForex notifies you once the account setup is completed, and you can fund and trade live.
Account types of RoboForex
With RoboForex, customers can choose from five account types, depending on their needs and objectives. Apart from these five, a free demo account is also available that allows you to test the market without financial risks. Muslim traders who comply with Sharia financial laws are also welcome to trade on an Islamic account.
Below, we review the five major account types that are available with the broker:
R Stocks Trader account

The RStocksTrader account is ideal for stock investments, but all other assets are available to trade. The fees on stocks are much lower whether you’re trading directly or on CFDs. Spreads can drop as low as 0.1 pips, and the commission on direct stocks is $0.02 per share. Note, that the commission on indices is variable. You can access all the asset offerings, including exotic stocks, pairs, and cryptocurrency CFDs. The leverage varies according to the asset. For instance, up to 1:300 is accessible on forex, but only 1:100 and 1:20 leverage is offered on indices and stocks, respectively. The minimum deposit for the account is $100, and it is available on the RTrader only.
Prime account

The Prime account is suitable for all assets and comes with excellent trading conditions. The minimum deposit for Prime is $100, and it is available on MT4, MT5, RTrader, and WebTrader.
28 forex pairs are available to trade on this account alongside cryptocurrencies CFDs, metals, and CFDs. The leverage offered can reach 1:300, according to regulations in your region. Spreads start from 0.0 pips and are floating. Commission per $1 million volume is $20. The account displays a trading history of up to one year.
ECN account

The ECN account gives traders access to greater liquidity and the best prices. The account spreads start from 0.0 pips, and a commission of $20 per $1 million traded volume applies. The minimum deposit is $100 and leverage of up to 1:500 is accessible. All 40+ forex pairs, together with the other markets are tradable on the MT4, MT5, cTrader, and RTrader. Account history is also viewable for up to 12 months.
Pro account

The Pro account is a standard STP account that requires a $10 minimum deposit. It works on all RoboForex platforms and allows you to trade all the instruments. The Pro is a zero-commission account, with a minimum spread of 1.3 pips. High leverage of up to 1:2000 is accessible, and RoboForex bonuses apply to the account. The trading history is also viewable for 12 months.
Pro Cent account

The Pro Cent account is ideal for financial market self-education. With $10, you can access the real market conditions. Seasoned traders use it for testing strategies and Expert Advisors (EA). It delivers all the assets, and leverage of up to 1:2000. There are no commission charges and the spreads start from 1.3 pips. The cent accounts work on the MetaTrader and RStocksTrader only.
Here is an overview for you:
| Account type: | Maximum Leverage | Loyality bonuses | Trading instruments |
|---|---|---|---|
| Pro Cent | 1:2000 | All offers | 36 currency pairs, metals, cryptocurrencies CFDs |
| Pro Standard | 1:2000 | All offers | 36 currency pairs, metals, CFD on US stocks, CFD on indices, CFD on oil, cryptocurrencies CFDs |
| ECN | 1:500 | Reduced number of promotions | 36 currency pairs, metals, CFD on US stocks, CFD on indices, CFD on oil, cryptocurrencies CFDs |
| Prime | 1:300 | Reduced number of promotions | 28 currency pairs, metals, CFD on US stocks, CFD on Indices, CFD on oil, cryptocurrencies CFDs |
| R StocksTrader | 1:300 | Not available | 12,000+ indices, real stocks, CFDs on stocks, Forex, ETF, CFDs on oil, CFDs on metals, CFDs on brazil stocks, cryptocurrencies CFDs |
Can you use a demo account on RoboForex?

Yes. RoboForex offers a free unlimited demo account that allows you to test the market beforehand. If you are new or inexperienced, this account can help you become conversant with the financial markets. You will not bear any financial risk since the market is a clone and not the real thing. Since it is a simulation, you will interact with real price movements, market sentiments, and conditions.
That is why many experienced traders use it to test their approaches before they enter the live market. As implied above, whatever you experience on this account will be the same as on a real account. So for newbies, it is crucial that you get it right on the demo before trading on the live account.
How to login into your RoboForex trading account

Logging in to trade is simple and only requires your username and password. Once you click on sign-in, it loads the member’s area. Here you will find a column for the username for password. Type them in the appropriate box and click on sign-in to get into your accounts.
Additional confirmation will be required if you enabled two-step verification on the account.
After entering the username and password, you would confirm the login by the verification instructions. It could be entering a unique one-time code that the broker sends to your phone or email. Or any other method that the broker requests to confirm you are you.
Verification – What do you need and how long does it take?

RoboForex must adhere to the financial regulations of its licensing bodies and operating regions. That is why the broker must request a government-issued ID and address proof from all its customers.
The broker does not accept work, school, or organization IDs for verification. Flight tickets are also invalid for proof of address confirmation. The accepted proof of address documents a recent utility bill receipt or bank account statements. The ID has to be a national ID or government-issued ID number, depending on the region.
Once you scan and upload these to the broker, it usually takes a few hours to verify. But sometimes, it can take over a day. If you have not heard from them after 48 hours, contact the support team.
Available payment methods for deposit and withdrawals
RoboForex offers various payment methods for easy deposits and withdrawals. Both services are generally free with popular payment options, though charges apply for withdrawals on some of the payment services.
The most popular choices are credit cards and debit cards, such as MasterCard, Visa, JCB, and UnionPay. Deposits are free on all of them, but withdrawals cost a 2.6% charge plus $1.3 on Credit Cards. Processing time for withdrawals can take between two to ten days, depending on the card. UnionPay settles faster than the rest.

E-wallet payment options are also popular and are cheaper than cards. Customers can use AstroPay, PerfectMoney, Neteller, AdvCash, Skrill, and NgangLuong wallets to make transfers. Deposits attract zero fees, but withdrawals can cost you between 0.5% to 1%, except for Neteller, which costs 1.9%. The broker boasts of instant settlement if you use an e-wallet, though the waiting period can get to 24 hours sometimes.
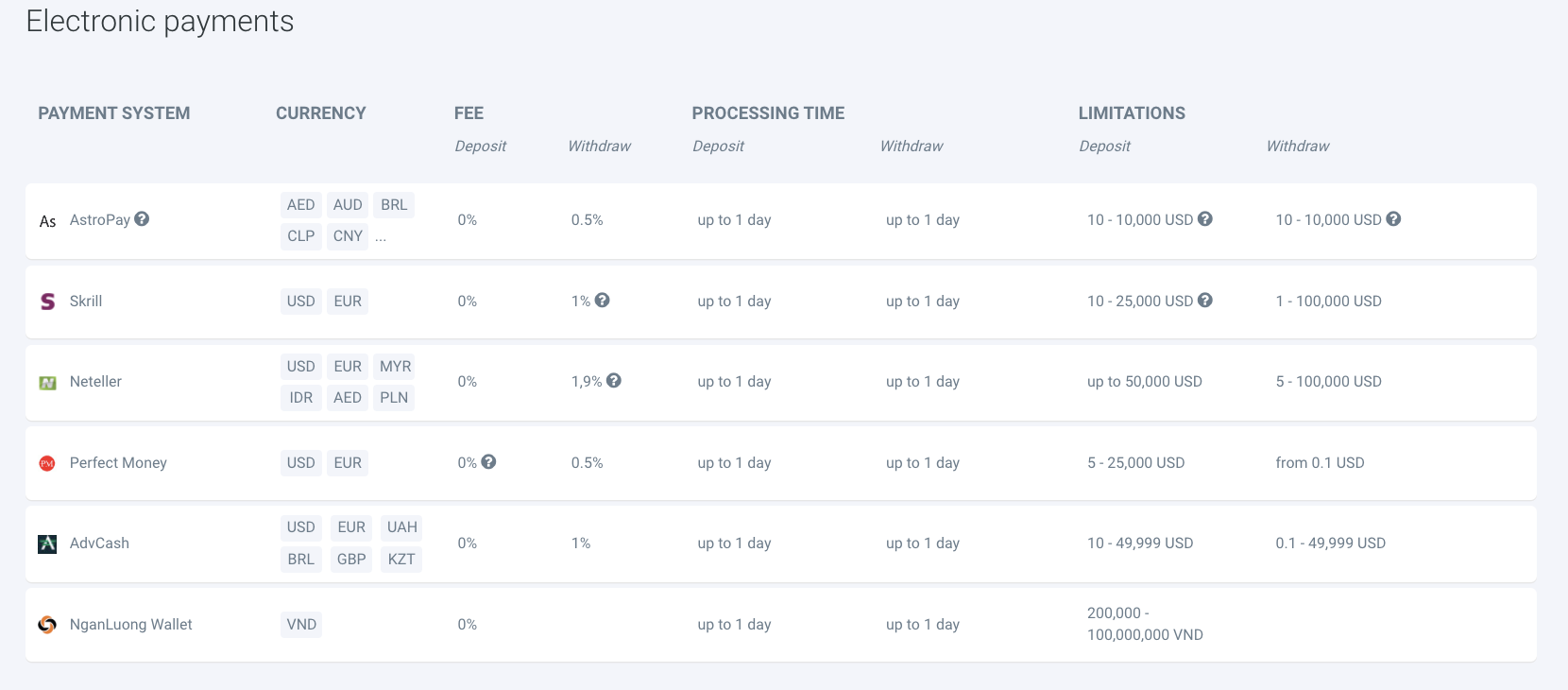
Bank transfers, both local and international, are accepted. Though they take longer to process and cost more. Deposits and Withdrawals using a SEPA member bank can take up to three days to settle. Deposit is free, but withdrawals cost a 1.5% fee. The Bank wire transfer method is not available in all regions. Withdrawal charges on this method range from 1.5% to 4%.
How to deposit money – The minimum deposit explained

To trade, you need to transfer money to your live account, and it must be at least the minimum deposit. The range is between $10 to $100, depending on the account type.
In the member’s area, click on the funds tab after signing in. Choose a deposit from the options and select your preferred money transfer option. Fill out the necessary details and confirm the information by clicking next. Enter your password to initiate the transfer and click on submit. The funds should reflect in the trading balance within the appropriate time.
Deposit bonuses

RoboForex offers a $30 bonus to new customers upon first deposits. Additionally, up to 120% deposit bonus is available to all customers using MT4 and MT5 platforms. The eligible customers are holders of the Pro-standard, Pro-cent, or ECN accounts. The profits earned from trading with the free credit are available for withdrawals anytime.
Several terms and conditions are attached, but traders get the opportunity for increased profits without the risk of leverage.
Withdrawal – How to withdraw your money on RoboForex

Withdrawal is as easy as moving funds into the account, though it takes longer and attracts charges. Click on the same funds tab in your member’s area. Select withdraw funds from the option and choose your preferred payment service.
Fill out the form by entering the necessary details and confirming the information. Click on submit and wait for the money to settle in your account. It can take from a few minutes to ten days, depending on the payment options used.
Support for traders
RoboForex offers multiple language support, which includes Chinese, Portuguese, Vietnamese, and more. You can reach them through phone or live chat on their webpage. There are different phone contact numbers for the different language support services. For English, the phone number is +65 3158 8389, while Chinese and Taiwanese contact numbers are +88 627 741 4290. Clicking on your preferred language on their website displays the appropriate support phone number.
| Customer care number: | Email support: | Live chat: | Availability: |
|---|---|---|---|
| English: +65 3158 8389 Chinese and Taiwanese: +88 627 741 4290 | [email protected] | Yes, available | 24/7 |
Education material – How to learn trading with RoboForex

RoboForex provides investment education resources for traders of all levels. Beginners’ resources include video tutorials, trading guides, and FAQs, which provide relevant basic information for newcomers.
Experienced traders can use a wealth of research and analysis tools, which includes economic calendars, analysis and forecasts, blogs, strategy builders, and charts.
Expert Advisors and social trading (through CopyFX) also serve as great education sources for every trader.
Additional fees on RoboForex
Fortunately, RoboForex does not charge additional or hidden fees. Dormant accounts do not attract fees. The only non-trading charge to worry about is the withdrawal costs.
Available countries and forbidden countries
RoboForex operates in 169 countries, with offices in specific regions. Unfortunately, the broker does not service customers based in the USA, Japan, Canada, Liberia, Australia, East Timor, and other restricted regions.
Conclusion – RoboForex is a safe broker and offers great conditions for traders

Based on our tests, we conclude that RoboForex is a legit and regulated broker worth trading with. The broker’s asset selections, though relatively narrow, offer appealing and profitable markets to speculate in. The only drawback we encountered are the withdrawal fees that apply. But taking its bonus offerings, competitive fees into account, and rich trading tools into account, we find that trading and investment can be good business with the broker. Therefore, it is easy to overlook these fees, as long as you use the best strategies that generate profits.
- Regulate online broker
- More than 15,000 different markets
- Start trading with only $ 10 minimum deposit
- Low spreads from 0.1 pips
- Variable commissions
- High leverage available (1:500+)
- Personal support 24/7
- Fast deposits and withdrawals
- No hidden fees!
Frequently asked questions:
Where is RoboForex located?
RoboForex’s head office is at 2118 Guava street, Phase 1 Belama, Belize City. There have branch offices in Cyprus, New Zealand, and the United Kingdom.
Is RoboForex a legit broker?
Yes, RoboForex is a legitimate broker. They are regulated by IFSC, and a member of the International Financial Commission.
Does RoboForex offer leverage?
Yes, RoboForex offers leverage ranging from 1:30 to 1:2000. Leverage trading is given based on financial regulations in each region and the asset. So the accessible leverage depends on the market instrument and jurisdiction.