Perdagangan opsi biner adalah cara membeli atau menjual saham atau aset apa pun dengan berspekulasi harganya. Walaupun trading mungkin terdengar mudah, kenyataannya tidak sesederhana itu.
Itu karena jika pergerakan harga suatu aset tidak dispekulasikan dengan benar, pedagang akan kehilangan semua jumlah yang diinvestasikan. Tetapi memprediksi pergerakan harga komoditas opsi biner secara akurat sedikit rumit.

Lihat video pola lengkap saya:
Sebagai seorang trader, Anda harus memperhatikan tren harga, fluktuasi pasar, dan berita keuangan. Dengan informasi yang relevan, Anda dapat membuat pilihan yang tepat. Salah satu alat yang dapat membantu Anda menganalisis pasar untuk menghasilkan keuntungan adalah grafik candlestick.
Senang mendengarnya:
- Grafik candlestick digunakan dalam perdagangan opsi biner untuk memvisualisasikan pergerakan harga aset, menunjukkan nilai pembukaan, penutupan, tertinggi, dan terendah dalam jangka waktu tertentu.
- Warna dan panjang setiap kandil menunjukkan tren pasar dan sentimen pedagang, dengan warna hijau/putih menunjukkan kenaikan harga dan merah/hitam menunjukkan penurunan.
- Mengenali pola kandil, seperti bullish, bearish, dan Doji, sangat penting untuk memprediksi pergerakan pasar dan membuat keputusan perdagangan yang tepat.
- Menggabungkan analisis kandil dengan indikator lain seperti RSI dan Bollinger Bands dapat meningkatkan strategi perdagangan dan meningkatkan peluang profitabilitas dalam perdagangan opsi biner.
Tapi apa itu grafik candlestick? Bagaimana Anda bisa membaca grafik candlestick? Apa saja polanya? Bagaimana cara melakukan analisis grafik? Nah, jawaban untuk semua pertanyaan ini dan lebih banyak lagi diberikan dalam panduan ini.

Apa itu grafik candlestick?
Grafik candlestick adalah alat yang digunakan oleh pedagang saat memperdagangkan opsi biner. Ini adalah cara mudah untuk menampilkan pergerakan harga aset yang diperdagangkan di pasar opsi dengan cara yang lebih baik.
Melalui grafik candlestick, seorang trader dapat dengan cepat memahami harga pembukaan, penutupan, tertinggi, dan terendah suatu komoditas dalam waktu tertentu. Karena grafik ini membantu trader memahami pergerakan harga dengan cepat, grafik ini menjadi alat yang andal untuk berdagang.
Lihat contoh grafik candlestick:

Dalam sebuah grafik, ada beberapa kandil, dan masing-masing kandil menandakan sesi perdagangan. Dengan melihat satu kandil, pedagang dapat memahami berapa harga suatu aset dalam waktu dekat.
Analisis pasar pola kandil lebih berhasil dan akurat daripada grafik perdagangan opsi biner lainnya. Itu berarti metode tinjauan pasar ini benar-benar berhasil.
Juga, grafik candlestick membantu trader profesional untuk mengetahui sentimen dasar pasar. Sehingga memberikan informasi yang lebih mendalam. Jadi, masuk akal mengapa trader menggunakan grafik candlestick.
Sejarah singkat grafik candlestick
Akan sangat bagus untuk mengetahui asal-usul bagan kandil untuk mendapatkan ide yang lebih baik tentang bagaimana itu dimulai.
Dengan baik, Grafik candlestick bukanlah konsep atau metode baru dalam menganalisis pasar. Sudah ada selama lebih dari satu dekade. Seorang pedagang beras Jepang membuat grafik perdagangan yang sukses ini pada abad ke-18 untuk memahami fluktuasi harga suatu barang.

Munehisa Homma, pencipta grafik candlestick, memahami bahwa emosi pedagang memainkan peran penting dalam fluktuasi harga komoditas. Jadi, dia memulai grafik candlestick, dan itu menjadi populer sejak saat itu.
Bagan ini telah menjadi pokok dari setiap platform perdagangan dan telah membantu beberapa pedagang untuk mendapatkan wawasan yang lebih jelas tentang pasar.
Candlestick vs. grafik batang
Grafik kandil dan batang – keduanya merupakan cara untuk merepresentasikan data perdagangan. Namun, ada perbedaan. Dibandingkan dengan diagram batang, candlestick lebih baik karena mudah dipahami.
Candlestick menyajikan informasi dengan lebih banyak warna dan visual. Artinya, ini menyoroti perbedaan harga dengan cara yang lebih baik.
Komponen kandil yang berbeda
Sangat penting untuk memahami komponen kandil untuk membaca tren harga komoditas pada sebuah grafik.
Grafik candlestick terbuat dari dua elemen berbeda, yaitu badan dan bayangan. Mereka datang dalam warna merah dan hijau. Di sini, bayangan mewakili harga tertinggi dan terendah perdagangan, sedangkan badannya menunjukkan kisaran buka dan tutup.
Bahkan perubahan kecil dalam warna tubuh atau ukuran bayangan menunjukkan fluktuasi yang signifikan dalam dunia perdagangan.

Warna
Dalam kandil warna hijau, diwakili dalam warna putih, bagian atas menunjukkan harga penutupan suatu aset, dan bagian bawah adalah harga pembukaan.
Artinya pasar bergerak naik karena harga penutupan lebih besar dari harga pembukaannya. Juga, jika kandil warna hijau berukuran panjang, berarti aset tersebut telah banyak dibeli dalam waktu tertentu.
Di sisi lain, dalam kandil warna merah, juga diwakili dalam warna hitam, bagian bawah menunjukkan harga penutupan, dan bagian atas menunjukkan harga pembukaan aset.
Jadi, ketika candlestick berwarna merah, Anda bisa mengartikan bahwa pasar sedang bergerak ke bawah. Itu karena harga pembukaannya lebih besar dari harga penutupannya. Kandil warna merah panjang menunjukkan bahwa suatu barang terjual banyak pada waktu tertentu.
Singkatnya, warna kandil di grafik mewakili pergerakan harga suatu item.
Bayangan

Seperti warna candlestick, bayangannya juga menunjukkan perubahan di pasar. Karena banyak pedagang gagal menganalisis data yang diwakili oleh sumbu dan ekor kandil, mereka kehilangan uang.
Jika bayangan berada di atas badan kandil, disebut sumbu. Namun jika bayangannya berada di bawah, disebut ekor. Juga, suasana pasar perdagangan dapat diartikan dengan panjang bayangan.
Bayangan atas dan bawah sebuah candle hampir tidak pernah sama ukurannya. Jika sumbu candlestick lebih panjang dari ekornya, hal ini menunjukkan bahwa pembeli menguasai pasar selama sesi perdagangan.
Demikian pula, jika ekor kandil lebih panjang dari sumbunya, itu berarti penjual pasar aktif selama sesi perdagangan. Terlepas dari posisinya, bayangan panjang biasanya muncul ketika tren akan berakhir.
Tetapi jika sumbu dan ekor kandil berukuran sama, ini menunjukkan keragu-raguan pedagang dan pembeli.
Apa yang diwakili oleh badan dan bayangan kandil dalam grafik?
Karena Anda tahu apa arti tubuh dan bayangan kandil, inilah arti ukuran, rasio, dan posisinya dalam grafik.

Ukuran badan kandil
Jika ukuran kandil tertentu dalam grafik terus meningkat, harganya juga naik. Tetapi jika panjang candlestick berkurang, itu menunjukkan kebalikannya, yaitu harga komoditas telah jatuh di pasar.
Tubuh kandil untuk jatah bayangan
Dibandingkan dengan shadow, jika badan candlestick panjang maka harga suatu komoditas di pasar telah bergerak naik mengikuti trend. Jika situasinya tetap sama dan arahnya tetap kuat, badan kandil akan semakin meningkat.
Di sisi lain, jika tubuh candlestick lebih kecil dari bayangan, itu berarti harga komoditas tidak bergerak mengikuti tren. Dengan demikian, ada ketidakpastian di pasar.
Posisi tubuh
Seiring dengan ukuran dan rasio candlestick, posisi tubuh juga memainkan peran penting.
Misalnya, jika kandil berukuran kecil dan memiliki ekor dan sumbu yang panjang, itu berarti harga aset tertentu telah kembali ke nilai aslinya. Biasanya terjadi ketika pembeli mencoba menaikkan harga sementara penjual menurunkannya.
Posisi selanjutnya adalah saat candlestick diletakkan di salah satu ujungnya dan memiliki bayangan panjang di sisi lainnya. Itu terjadi ketika harga aset telah bergerak ke arah tertentu, baik oleh pembeli atau penjual.
(Peringatan risiko: Modal Anda bisa berisiko)
Psikologi kandil untuk perdagangan Opsi Biner

Dengan candlestick, Anda dapat membaca psikologi pasar dalam perdagangan Binary Options. Dari pengalaman kami, cara terbaik untuk membaca pikiran trader lain adalah dengan menafsirkan sumbu pada candlestick. Lihat gambar di bawah ini:
Sumbu adalah salah satu sinyal terbaik jika Anda ingin mengetahui ke arah mana pasar akan bergerak. Banyak orang yang memperdagangkan kandil, artinya sebelum sumbu, pedagang lain akan melihat kandil secara penuh. Pemain lain yang lebih kuat masuk ke pasar dan mendorong pasar kembali. Terjadi penolakan, dan kita melihat sumbu sebagai hasilnya. Banyak trader yang kini terjebak ke arah yang salah, dan mereka harus menutup posisinya.
Dengan menggunakan sumbu dalam perdagangan Binary Options, kita dapat menghasilkan hit rate yang lebih tinggi!
Lihat video saya tentang itu:
Bagaimana cara membaca grafik candlestick?
Seorang trader dapat memeriksa harga suatu aset di pasar dengan menganalisis dua bagian candle, yaitu badan dan bayangan. Setiap kandil di grafik mewakili pergerakan harga suatu aset dalam waktu tertentu, seperti satu hari, satu minggu, atau satu bulan.
Selain itu, setiap grafik candlestick memiliki empat titik data, yaitu high, low, open, dan close. Jadi, jika seorang pedagang memiliki waktu perdagangan yang tetap, grafik akan diperbarui sesuai dengan itu.
Anda dapat menganalisis bayangan dan tubuh candlestick untuk mengetahui mood pasar. Dan berdasarkan spekulasi Anda, Anda bisa melakukan perdagangan.
Penjelasan pola candlestick yang berbeda:
Meskipun ada beberapa pola, tidak semuanya bekerja secara efektif. Artinya mereka tidak akan membantu Anda memprediksi pasar dengan benar. Dan ini bisa membuat Anda kehilangan uang dalam jumlah yang cukup besar.
Pola candlestick terbagi menjadi dua kategori, yakni pola bullish dan bearish. Berdasarkan keduanya, pedagang dapat memahami pola yang berbeda.
Pola Bullish
Ketika pembeli mendominasi pasar dibandingkan penjual, pola bullish terbentuk. Artinya harga penutupan lebih besar dari harga pembukaan. Warna hijau atau putih melambangkan kehadiran bullish di pasar.

Pola Bearish
Pola bearish merupakan kebalikan dari pola bullish. Artinya penjual menguasai pasar. Setelah melihat pola bearish, dapat disimpulkan bahwa harga pembukaan lebih tinggi dibandingkan harga penutupan. Juga diwakili oleh warna merah atau hitam.
Berikut adalah beberapa pola candlestick bearish dan bullish yang berguna yang dapat meningkatkan profitabilitas perdagangan Anda.
(Peringatan risiko: Modal Anda bisa berisiko)
Perdagangan Doji
Ketika pasar biner tidak dikendalikan oleh bearish atau bullish, itu menunjukkan keragu-raguan pasar. Dan saat itulah pola Doji terbentuk. Pola ini dibagi lagi menjadi empat bagian.
Empat pola Doji yang berbeda adalah Doji umum, Doji capung, Doji Gravestone, dan Doji berkaki panjang. Tetapi tidak semuanya mewakili keragu-raguan pasar. Trader dapat dengan mudah menemukan pola Doji di grafik candlestick karena diwakili oleh bentuk salib.
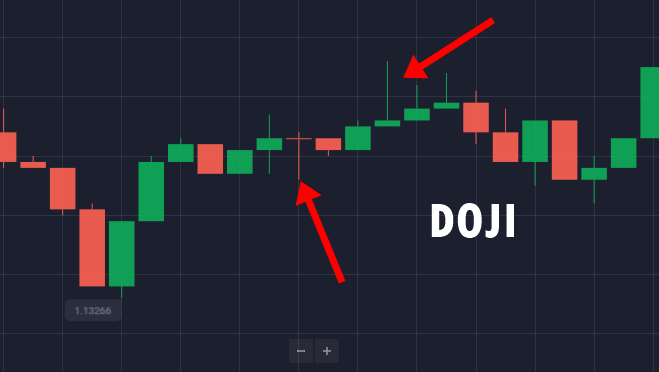
Keuntungan dari metode Doji
Saat trading, jika pasar bergerak ke atas dan ada pola Doji, Anda dapat menyimpulkan bahwa aksi jual akan dimulai dengan memperlambat momentum beli.
Jika Anda keluar dari pasar berdasarkan analisis pola Doji, Anda dapat memperoleh keuntungan yang cukup besar. Tetapi penting untuk memastikan bahwa pasar menunjukkan apa yang telah ditunjukkan oleh pola Doji. Jika tidak, Anda bisa menghadapi kerugian besar.
Memahami varian candlestick yang berbeda
Berikut adalah empat varian pola Doji yang populer dan apa yang ditunjukkannya.

Doji Standar
Doji standar dalam grafik candlestick berarti harga beli dan jual adalah sama. Ini diwakili oleh salib atau tanda plus.
Dragonfly Doji
Dragonfly Doji adalah kandil berbentuk “T” di grafik. Ini memiliki tubuh kecil di bagian atas, diikuti oleh sumbu panjang yang lebih rendah. Pola ini menunjukkan bahwa pasar dibuka pada harga tinggi dan turun. Namun, itu meningkat ke tingkat harga yang sama di akhir perdagangan.
Singkatnya, dragonfly Doji terbentuk saat harga turun, tetapi pembeli mendorongnya ke atas pada menit terakhir.
Batu Nisan Doji
Gravestone Doji adalah kebalikan dari Dragonfly Doji. Pola ini terbentuk ketika harga penutupan dan pembukaan suatu aset berada pada level bawah yang sama.
Gravestone Doji menunjukkan bahwa ketika pasar dibuka, harganya tiba-tiba didorong ke bawah oleh penjual. Pedagang dapat memperoleh keuntungan yang baik jika mereka memperdagangkan pola Doji nisan.
Doji berkaki panjang
Doji berkaki panjang terlihat mirip dengan Doji biasa. Namun, ia memiliki sumbu atas dan bawah yang relatif lebih panjang. Sumbu panjang menunjukkan keragu-raguan pasar.
Saat Anda melihat Doji berkaki panjang, cobalah untuk tidak memperdagangkan opsi biner (Anda harus tahu kapan), karena dapat membuat Anda kehilangan semua uang yang diinvestasikan. Setelah sumbu dipersingkat, Anda dapat berdagang.
(Peringatan risiko: Modal Anda bisa berisiko)
Perdagangan terobosan

Perdagangan breakout pada grafik kandil menunjukkan pergerakan harga suatu aset. Harga suatu komoditas telah melampaui level resistance atau di atas level support.
Level resistance atau support juga dapat dilihat sebagai titik stop loss atau entry level yang dapat membantu trader mendapatkan profitabilitas yang besar.
Ketika harga bergerak melampaui level resistance atau support, trader memiliki dua pilihan. Pertama, mereka dapat keluar dari pasar jika mereka tidak ingin harga keluar. Meninggalkan pasar dapat membantu para pedagang menyelamatkan diri dari kerugian besar. Kedua, para trader yang menunggu breakout bisa langsung masuk ketika breakout terjadi untuk mendapatkan profit yang signifikan.
Setelah breakout, volatilitas pasar meningkat, dan harga bergerak menuju arah breakout. Karena breakout menunjukkan fluktuasi harga yang lebih besar dan lebih banyak volatilitas, ini membawa lebih banyak profitabilitas.
Cara kerja perdagangan breakout
Untuk berdagang menggunakan pola ini, Anda perlu menganalisis dua hal. Pertama, konsistensi menyentuh level resistance. Jika harga aset telah menyentuh level resistance dan support beberapa kali, analisisnya menjadi lebih valid.
Dan kedua, lamanya waktu bermain. Jika level support dan resistance tetap di posisi mereka untuk waktu yang lama, hasilnya lebih menguntungkan.
Trader dapat dengan cepat mengidentifikasi breakout pola grafik karena umumnya ditemukan pada titik awal sebuah tren. Jadi, jika Anda tahu bagaimana mengidentifikasi breakout di pasar, Anda dapat meningkatkan profitabilitas Anda.
Perdagangan breakout palsu
Pola trading candlestick selanjutnya adalah fake breakout. Pola ini adalah kebalikan dari breakout, dan persis seperti apa kedengarannya.

Satu hal yang membuat pola breakout palsu menarik adalah ketidakpastiannya. Harga bergerak sedemikian rupa sehingga para pedagang berasumsi bahwa harga mungkin akan pecah. Jadi, mereka berdagang; namun, harga menipu trader dengan kembali ke level yang sama.
Penembusan palsu adalah salah satu pola perdagangan penting yang bahkan dapat dipahami dan diidentifikasi oleh pedagang yang tidak berpengalaman. Penembusan palsu dalam grafik perdagangan mewakili satu dari dua hal. Entah tren harga akan segera berlanjut, atau harga akan segera berubah.
Situasi ini muncul ketika pedagang mencoba memasuki pasar ketika semuanya stabil. Namun, ketika mereka membuat entri, harganya balik. Dengan demikian, kerangka waktu penting dalam pelarian palsu.
Bagaimana cara memperdagangkan breakout palsu?
Penembusan palsu dapat terjadi dalam kondisi pasar dan tren harga apa pun. Untuk berdagang dengan sukses dalam pelarian palsu, pedagang perlu melakukan beberapa hal.
- Perhatikan berita keuangan.
- Cobalah untuk memahami alasan di balik pelarian palsu.
- Menilai pelarian palsu dan bagaimana hal itu akan berdampak pada tren harga.
- Perhatikan titik ekstrim di pasar.
Jika Anda tidak ingin terjebak perdagangan breakout palsu, Anda bisa menunggu harga aset ditutup di luar kisaran. Jika ini terjadi beberapa kali, Anda dapat mengasumsikan bahwa tren harga akan mulai lagi.
(Peringatan risiko: Modal Anda bisa berisiko)
Perdagangan garis tren
Garis tren adalah cara untuk mengetahui tren harga suatu aset di pasar. Mengidentifikasi trendline dapat membantu pedagang untuk melakukan perdagangan yang sukses. Itu karena trendline membantu pedagang mengetahui apakah pasar bekerja sesuai keinginan mereka atau tidak.
Garis tren adalah alat yang sederhana dan mudah digunakan, dibagi menjadi beberapa kategori, yaitu garis tren turun dan garis tren naik.

Garis tren naik di grafik candlestick menunjukkan ada kelebihan jumlah pembelian di pasar. Itu berarti harga suatu aset kemungkinan akan meningkat. Di sisi lain, garis tren turun menunjukkan tekanan pasokan. Garis tren turun membuat harga turun.
Selain itu, jika garis trennya datar, berarti harga pasar bergerak ke arah yang stabil. Trader tidak boleh mengambil posisi long ketika melihat garis tren menurun.
Garis tren dalam grafik dibuat dengan menghubungkan serangkaian harga. Untuk mendapatkan gambaran yang lebih baik, pedagang hanya harus fokus pada titik ayunan utama. Setelah Anda membuat garis tren, Anda dapat mengidentifikasi pasar dengan cepat.
Anda harus berdagang di sekitar garis tren untuk meraih peluang perdagangan yang lebih baik dan meningkatkan profitabilitas Anda. Untuk memasuki pasar, Anda bisa menunggu sampai harga menembus trendline.
Pola Bullish/Bearish Engulfing

Pola candlestick populer lainnya adalah pola bullish/bearish engulfing. Ini adalah salah satu dari sedikit pola yang dapat dengan mudah diidentifikasi dan berisi semua informasi penting.
Pola bullish engulfing pada grafik candlestick menunjukkan tren turun. Itu berarti ada kenaikan pola beli di pasar. Dua lilin hijau mewakilinya. Lilin hijau kedua menelan tubuh lilin merah sebelumnya.
yang bearish pola menelan adalah kebalikan dari pola bullish engulfing. Pola ini terjadi ketika harga aset turun karena lebih banyak penjual memasuki pasar. Pola ini diwakili oleh dua lilin merah di mana lilin merah menelan lilin hijau berikutnya.
Saat Anda melihat pola bearish atau bullish, ini berarti akan ada sebuah pembalikan dalam tren. Jika trader memegang posisi pada suatu aset yang tren harganya akan segera berakhir, mereka dapat menggunakan pola ini untuk keluar dari pasar yang sedang tren.
(Peringatan risiko: Modal Anda bisa berisiko)
Pola Bintang Kejora/Bintang Sore

Itu bintang Timur dan pola bintang malam sedikit berbeda dari pola bullish engulfing dan bearish engulfing karena mencakup tiga candle daripada dua.
Pola bintang pagi dapat didefinisikan sebagai representasi visual dari tiga lilin yang membentuk tren turun. Kehadiran bintang pagi di grafik candlestick menunjukkan tren harga akan berbalik arah.
Pola bintang malam pada grafik candlestick adalah kebalikan dari pola bintang pagi. Ini mewakili tren naik di pasar. Pola bintang malam juga menceritakan tentang pembalikan harga aset di masa depan.
Pola ini umumnya muncul ketika pasar menunjukkan harga terendah yang lebih tinggi atau harga tertinggi yang lebih tinggi. Jika Anda ingin memperdagangkan pola kandil Evening Star, jangan menunggu harga turun, karena Anda mungkin kehilangan perdagangan.
Pola Tindik
Pola menusuk terbentuk saat pullback atau di akhir tren turun. Lebih lanjut dibagi menjadi dua kategori, yaitu candle bearish dan candle bullish.
Pola ini dapat ditemukan di grafik ketika candle kedua, yaitu candle bullish, ditutup di tengah candle pertama, yaitu candle bearish. Situasi ini muncul di pasar downtrend.
(Peringatan risiko: Modal Anda bisa berisiko)
Strategi grafik kandil yang terbukti untuk pemula
Saya memperkenalkan Anda pada dua strategi kandil yang telah terbukti untuk memperdagangkan opsi biner. Saya sering menggunakannya ketika saya menyadari bahwa pasar sedang berubah.
Perdagangan Dukungan dan Perlawanan
Strategi pertama yang saya suka gunakan dalam perdagangan opsi biner 60 detik. Saya ingin mengilustrasikannya dengan perdagangan praktis.
Dalam contoh ini, saya memperdagangkan EUR/USD. Pertama, saya mengatur jangka waktu menjadi 60 detik. Kemudian saya beralih antara grafik 60 detik dan 5 menit dan melihat dari dekat level support dan resistance serta garis tren. Strategi ini bertujuan untuk memprediksi candle berikutnya untuk menghasilkan profit dengan trading singkat 60 detik.
Untuk gambaran yang lebih baik, saya menggambar level support dan resistance:

Strategi ini mengasumsikan perdagangan dalam kisaran support dan resistance. Saya kira harganya akan naik, tapi saya belum memulai perdagangan dan sedang menunggu lilin konfirmasi.

Seperti yang Anda lihat pada gambar di atas, ada Hammer Candle. Palu adalah sinyal bagus bahwa pasar akan bergerak naik.
Sebelum saya memulai perdagangan, saya berkonsultasi dengan indikator RSI dan Bollinger Band. Ini harus dilakukan dengan cepat karena perdagangan bersifat jangka pendek. Kedua indikator perdagangan tersebut menunjukkan bahwa pasar akan melakukan pergerakan naik dalam jangka pendek. Karena ada pola candlestick hammer yang mengkonfirmasi asumsi saya, saya membuka order beli.
Strategi perdagangan sederhana, yang saya hasilkan 955 euro dari 500 euro dalam perdagangan ini. Strateginya sederhana namun efektif karena kami memiliki 3 kali konfirmasi bahwa kursus akan berjalan sesuai asumsi. Indikator RSI, sebagai indikator momentum, membantu memprediksi kecepatan dan arah tren.
Kombinasikan kandil dengan indikator lain
Cara terakhir Anda dapat berdagang kandil adalah dengan menggabungkan kandil dengan indikator lain. Ketika Anda melakukan ini, Anda memaksimalkan peluang Anda untuk menghasilkan lebih banyak keuntungan. Dengan demikian, Anda tidak menanggung lebih banyak kerugian. Dengan cara ini, Anda juga membuka begitu banyak kemungkinan perdagangan yang berbeda untuk diri Anda sendiri. Dan jika waktu Anda tepat, Anda juga dapat membuka pintu kesuksesan dan menjadi master trader.

Bagaimana cara membaca satu lilin?
Jika Anda memilih untuk memperdagangkan satu kandil, Anda perlu mengetahui cara yang tepat untuk membaca satu kandil.
Saat Anda memperdagangkan satu lilin, dan Anda melihat bayangan atas yang panjang, harga akan turun. Itu karena investor ingin menjual. Di sisi lain, jika Anda mengamati bayangan panjang ke bawah, itu berarti harga pasar sedang naik.
Demikian pula, jika ada pola candle Doji, itu menunjukkan keragu-raguan. Dan hal ini menunjukkan harga pembukaan dan penutupan yang sama. Terakhir, jika Anda melihat pola palu di grafik selama perdagangan satu kandil, ini berarti pembeli sedang beraksi.
(Peringatan risiko: Modal Anda bisa berisiko)
Kesimpulan: Gunakan pola grafik untuk memenangkan Opsi Biner
Sementara beberapa grafik dapat digunakan untuk mewakili pergerakan harga di pasar opsi biner, lebih baik memilih grafik candlestick. Itu karena mudah dimengerti dan menceritakan tentang suasana pasar yang lengkap.
Namun untuk mendapatkan keuntungan, penting untuk memilih pola kandil yang memberikan informasi detail tentang tren harga. Dengan informasi yang benar, Anda dapat berspekulasi pasar dengan benar dan menghasilkan perdagangan yang menguntungkan.
Untuk menjadi trader yang sukses, Anda dapat memilih pola candlestick yang tepat, tetap pada strategi terperinci, dan jangan pernah berhenti belajar.
Untuk bacaan lebih lanjut, Anda juga dapat membaca kami Panduan pola ABCD untuk Opsi Biner atau Panduan Pola Harmonik.
Pertanyaan yang sering diajukan tentang Grafik Candlestick:
Apa tujuan utama grafik candlestick dalam perdagangan opsi biner?
Grafik kandil digunakan untuk menampilkan pergerakan harga aset dalam perdagangan opsi biner, membantu pedagang dengan cepat memahami harga pembukaan, penutupan, tertinggi, dan terendah dalam jangka waktu tertentu.
Apa yang ditunjukkan oleh warna dan panjang kandil?
Warna dan panjang kandil menunjukkan tren pasar dan sentimen trader. Hijau atau putih menunjukkan kenaikan harga, sedangkan merah atau hitam menunjukkan penurunan.
Apa pentingnya tubuh dan bayangan candlestick?
Badan kandil mewakili kisaran harga pembukaan dan penutupan suatu aset, sedangkan bayangan (atau sumbu/ekor) menunjukkan harga tertinggi dan terendah perdagangan. Perubahan ukuran dan warna dapat menandakan fluktuasi pasar yang signifikan.
Apa perbedaan antara grafik kandil dan grafik batang?
Grafik kandil lebih disukai daripada grafik batang karena grafik ini menyajikan informasi secara lebih visual dengan warna, menyoroti perbedaan harga dengan lebih efektif.
Apa sajakah pola kandil yang umum dalam perdagangan opsi biner?
Pola candlestick yang umum mencakup pola bullish dan bearish, pola Doji (menunjukkan keragu-raguan pasar), dan formasi spesifik seperti Dragonfly Doji dan Gravestone Doji, masing-masing memberikan wawasan tentang tren pasar dan potensi pembalikan.
Apa pentingnya menggabungkan analisis candlestick dengan indikator lainnya?
Menggabungkan analisis kandil dengan indikator lain seperti RSI dan Bollinger Bands dapat meningkatkan strategi perdagangan, meningkatkan peluang profitabilitas dengan memberikan pandangan yang lebih komprehensif tentang tren pasar dan potensi pergerakan harga.








Saya ingin belajar lebih banyak
Hai informasi yang sangat membantu
terima kasih banyak, baru saja mulai berdagang biner.