Se você negocia em uma plataforma de corretora, precisa de informações sobre os métodos de pagamento. Qual é a maneira mais fácil e barata de negociar opções binárias? Por que é vantajoso usar diferentes métodos de pagamento? Neste artigo, você encontrará informações completas sobre transações com cartões VISA usando os melhores corretores de opções binárias.
Muitos provedores de pagamento com cartão de crédito recentemente sistemas de segurança melhorados. Tais sistemas garantem que as transações serão protegidas. Vários corretores de negociação de opções importantes têm acordos especiais com as principais empresas de cartão de crédito para atualizar suas negociações.
Estas são as 3 melhores corretoras de opções binárias que aceitam cartão Visa:
Corretor:
Aceita cartão VISA:
Vantagens:
Conta:

sim
- Maior retorno
- Execução mais rápida
- Sinais
- negociação 24/7
- Demo grátis
- $ 10 min. depósito
95%+ retorno
(Aviso de risco: seu capital pode estar em risco)

sim
- Amigo do usuário
- Transferências
- Suporte 24/7
- Alto retorno
- Demo grátis
- $ 10 min. depósito
Até 100% retorno
(Aviso de risco: seu capital pode estar em risco)

sim
- Bônus
- negociação 24/7
- Negociação social
- Demo grátis
- $ 50 min. depósito
92%+ retorno
(Aviso de risco: seu capital pode estar em risco)
Veja a lista das três melhores corretoras de opções binárias que aceitam cartões Visa:

- Quotex – Nosso corretor Visa número um
- IQ Option – Taxas baixas e spreads brutos
- Pocket Option – Comece a negociar com um clique
O que você vai ler neste Post
(Aviso de risco: seu capital pode estar em risco)
Sobre a Visa – Introdução ao sistema de pagamentos

Se você fizer pagamentos ou depósitos usando um cartão de crédito ou débito, você deve ser cauteloso com o número de pagamentos que fará se estiver investindo com fundos emprestados. Em particular, você deve garantir que não está arriscando mais do que pode perder.
Você deve sempre tentar evite tomar uma atitude entusiasta e perder quantias significativas de dinheiro porque não pertence a você. Se você não tomar as medidas adequadas para evitar tal comportamento, poderá eventualmente se encontrar em dívidas consideráveis.
Uma desvantagem importante de utilizar um cartão de crédito em vez de um cartão de débito é a custos de juros altos. Como resultado, utilizar um cartão de crédito para fazer pagamentos tornará consideravelmente difícil manter receitas consistentes.
É porque, mesmo que você ganhe com as negociações depois de fazer depósitos por meio dessa opção de serviço de depósito, os juros acumulados vão corroer seus ganhos.
No entanto, os depósitos efetuados com cartões bancários VISA em contas de corretagem são rápidos. As retiradas geralmente levam 1 dia útil para serem processadas. Se você estiver sacando dinheiro usando um Cartão VISA pela 1ª vez, algumas empresas podem exigir algum tipo de verificação do usuário.
Isso pode incluir exigir um fatura do cartão de crédito de seus bancos ou um recibo de transferência de fundos com a identidade do usuário, localização e qualquer outra informação com a qual a corretora possa estar preocupada.
Outros também podem solicitar uma fotografia do usuário segurando o cartão ou um close-up do verso e da frente do cartão mostrando os detalhes do cartão, data de validade, Código CVC/CVV e nome do titular do cartão. A solicitação de retirada do usuário é processada após a verificação. As transferências subsequentes geralmente são rápidas e não requerem todas essas informações.
Algumas empresas também trabalham com VISA para emitir cartões de crédito para seus clientes. Isso permite que os usuários recarreguem o cartão de crédito e o usem para financiar suas carteiras de negociação de opções, bem como fazer saques de suas respectivas contas de corretagem. Esses cartões VISA são então usados para retirar dinheiro de caixas eletrônicos.
(Aviso de risco: seu capital pode estar em risco)
Visa é seguro? Segurança do uso de cartões Visa para comerciantes

A segurança das transações com cartão Visa, no entanto, é uma grande preocupação para proprietários de empresas e clientes. Nesta seção, veremos os recursos de segurança dos cartões Visa e como eles evitam roubos e compras ilegais.
- Prevenção e proteção contra fraudes – O Visa Card fornece várias camadas de segurança para evitar fraudes e transações não autorizadas. A Visa também usa criptografia avançada e tecnologia de tokenização para proteger os dados do titular do cartão durante as transações.
- Política de Responsabilidade Zero da Visa – garante que os titulares de cartões não sejam responsabilizados por quaisquer cobranças fraudulentas feitas em seu cartão. Se o titular do cartão relatar qualquer transação não autorizada, a Visa investiga o caso e reembolsa o titular do cartão pelo valor total da transação não autorizada.
- Tecnologia de chip EMV – vem com tecnologia de chip EMV, que fornece uma camada adicional de segurança contra fraudes com cartões falsificados. Os chips EMV geram um código único para cada transação, tornando difícil para os fraudadores duplicar os detalhes do cartão.
- Verificado pela Visa – é uma camada extra de segurança que exige que os titulares de cartão forneçam uma senha ou um código exclusivo para concluir as transações online. Esse recurso garante que apenas o titular do cartão autorizado possa concluir a transação, reduzindo o risco de fraude.
Portanto, os cartões Visa são uma escolha segura para os comerciantes.
Prós e contras do uso de cartões Visa para comerciantes
Os cartões Visa têm muitos benefícios para os comerciantes, incluindo reconhecimento universal, baixas taxas de transação e um curto tempo de processamento. Muitas empresas de cartões Visa possuem medidas de segurança para monitorar e prevenir atividades fraudulentas, fornecendo uma camada adicional de segurança para os titulares de cartões contra fraudes e compras não autorizadas.
Mas também há desvantagens, como as taxas. Vamos dar uma olhada nos prós e contras.
- Ampla aceitação
- Recursos de segurança
- Velocidade e conveniência
- Recompensas e Reembolso
- Construção de pontuação de crédito
- Altas taxas de transação
- Taxas de transação estrangeira
- Risco de gastos excessivos
- Taxas sobre saldo de crédito
(Aviso de risco: seu capital pode estar em risco)
Os 3 melhores corretores de opções binárias que aceitam cartões Visa
Vamos conhecer mais as vantagens dos três melhores corretores de opções binárias que aceitam cartões Visa.
#1 Quotex – Nosso corretor Visa número um

Quotex está entre os principais corretoras de opções proeminentes e comumente usadas. É uma corretora on-line autorizada e regulamentada lançada em 2020. A empresa fornece indicações de mercado e replica a negociação em uma plataforma baseada na Internet bem desenvolvida e exclusiva.
Mais especificamente, a corretora é um marca licenciada da Awesome Ltd, que tem sede em Seychelles. Esta empresa é autorizada pelo IFMRRC – Centro de Regulação das Relações com os Mercados Financeiros Internacionais, conforme detalhes no site principal. Em novembro de 2020, se tornará um completamente registrado corretagem.
Recursos
Este site de negociação de opções binárias on-line oferece aos clientes uma variedade de instrumentos para aumentar suas possibilidades de ganhar com uma negociação. É simples de operar e incrivelmente protegido. As principais características da Quotex incluem:
- Os comerciantes podem aproveitar as boas-vindas bônus e recompensas na Quotex
- existe uma gratuidade Conta de demonstração Quotex acessível
- Você pode começar depositando simplesmente US $ 5
- A taxa de pagamento é bastante alta, cerca de 98 por cento
- Está acessível em mais de 19 idiomas diferentes em todo o mundo.
- Tem troca de cópia opções de assistência acessíveis, bem como uma seleção de sinais de negociação.
- Durante uma transação, incentivos de até 40% são oferecidos.
Aplicativo móvel
Seu aplicativo móvel oferece uma interface de usuário incrivelmente simples, incluindo todas as funcionalidades presentes no site da internet. Ele funciona rapidamente e fornece atualizações sobre alterações de preços em tempo real.

Tipos de contas
Conta Demo
O corretor fornece aos usuários um sem risco Quotex conta de demonstração sem nenhum custo. Para começar a negociar em uma conta demo, os usuários não precisam fornecer detalhes pessoais. É grátis e inclui $10.000 em fundos falsos. Você pode recarregar a Conta Demo gratuitamente a qualquer momento.
Conta Básica
Quotexs Conta Básica fornece acessibilidade ao setor de negociação em tempo real por apenas $10. Cartões de crédito/débito, bem como carteiras digitais, como Neteller, Webmoney, Advcash, Skrill, e PerfectMoney, podem ser usados para fazer pagamentos. Quotex é um corretora que aceita criptomoedas e depósitos criptográficos também.
Conta Profissional
Investidores experientes têm direito a um ambiente comercial favorável. Quotex concede o nível Pro para clientes com saldo de conta superior a 1000 USD. Os usuários Pro recebem um serviço de alto nível, um pagamento maior do que os titulares de contas básicas e um gerenciador de fundos separado. Contas profissionais se beneficiam de pagamentos mais altos e desembolsos de fundos mais rápidos.
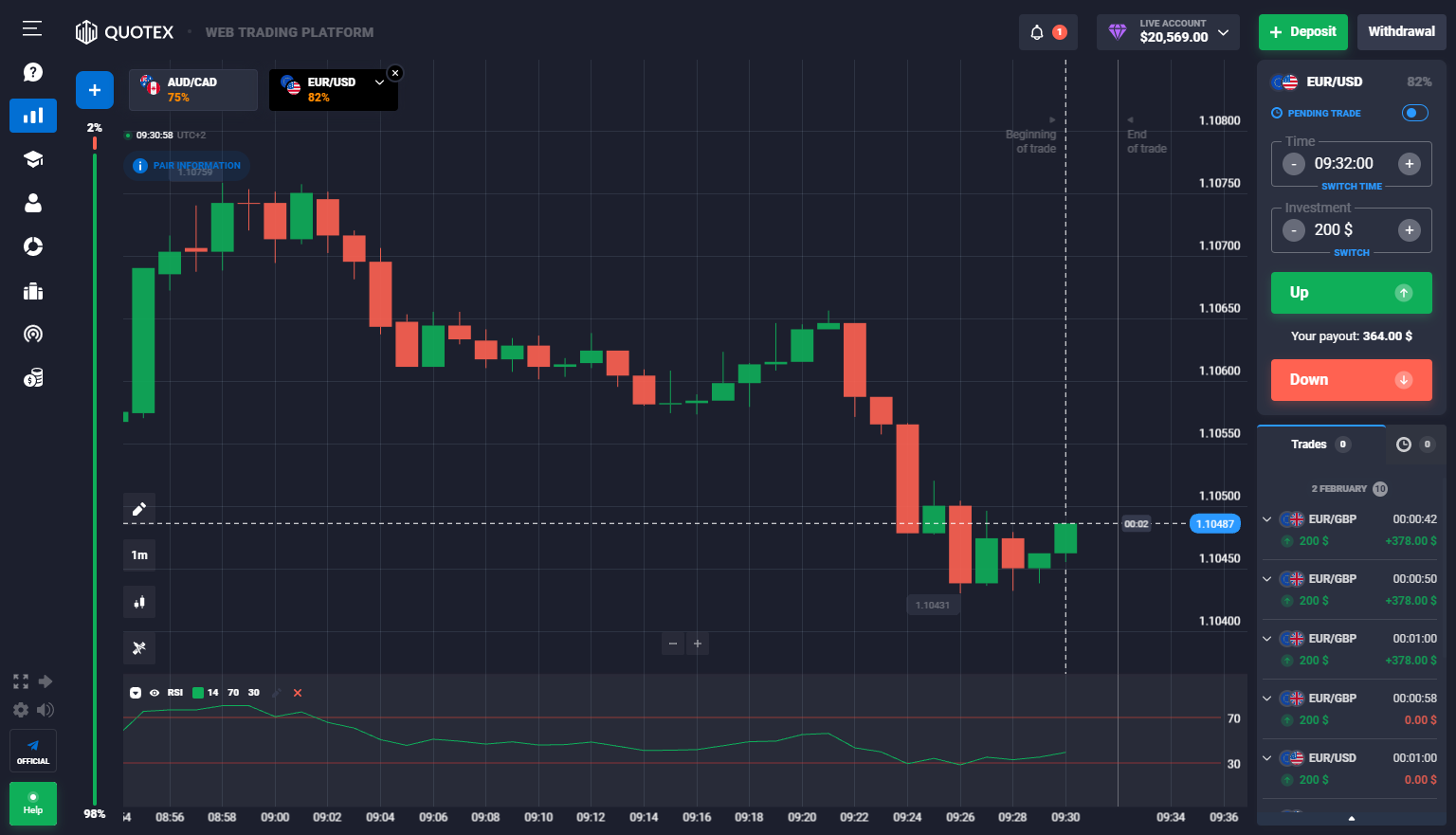
Receba um bônus de depósito grátis de 50% em Quotex com nosso código promocional “boboker50“
Conta VIP
Operadores experientes com investimentos maiores exigem a consideração total da empresa. Quotex fornece classificação VIP para clientes com saldo de conta superior a 5.000 USD. Usuários VIP recebem serviço premium, um retorno maior, e um supervisor de conta pessoal. Os usuários VIP também recebem dinheiro mais rápido e gratuito Retiradas Quotex.
- Receita máxima: até 98%
- Comércio mínimo: $1
- Mínimo depósito Quotex quantia: $10
- Bens: ações, índices, criptomoedas, commodities e Forex
- Pontos de venda: versão desktop, aplicativo móvel, Android e Apple
- Métodos de Pagamento: Cartões de crédito ou débito, criptos, Carteiras eletrônicas
- Depósitos com Visa: Disponível
- Saques com Visa: Disponível
- Taxas adicionais de visto: Não
(Aviso de risco: seu capital pode estar em risco)
#2 IQ Option – Taxas baixas e spreads brutos
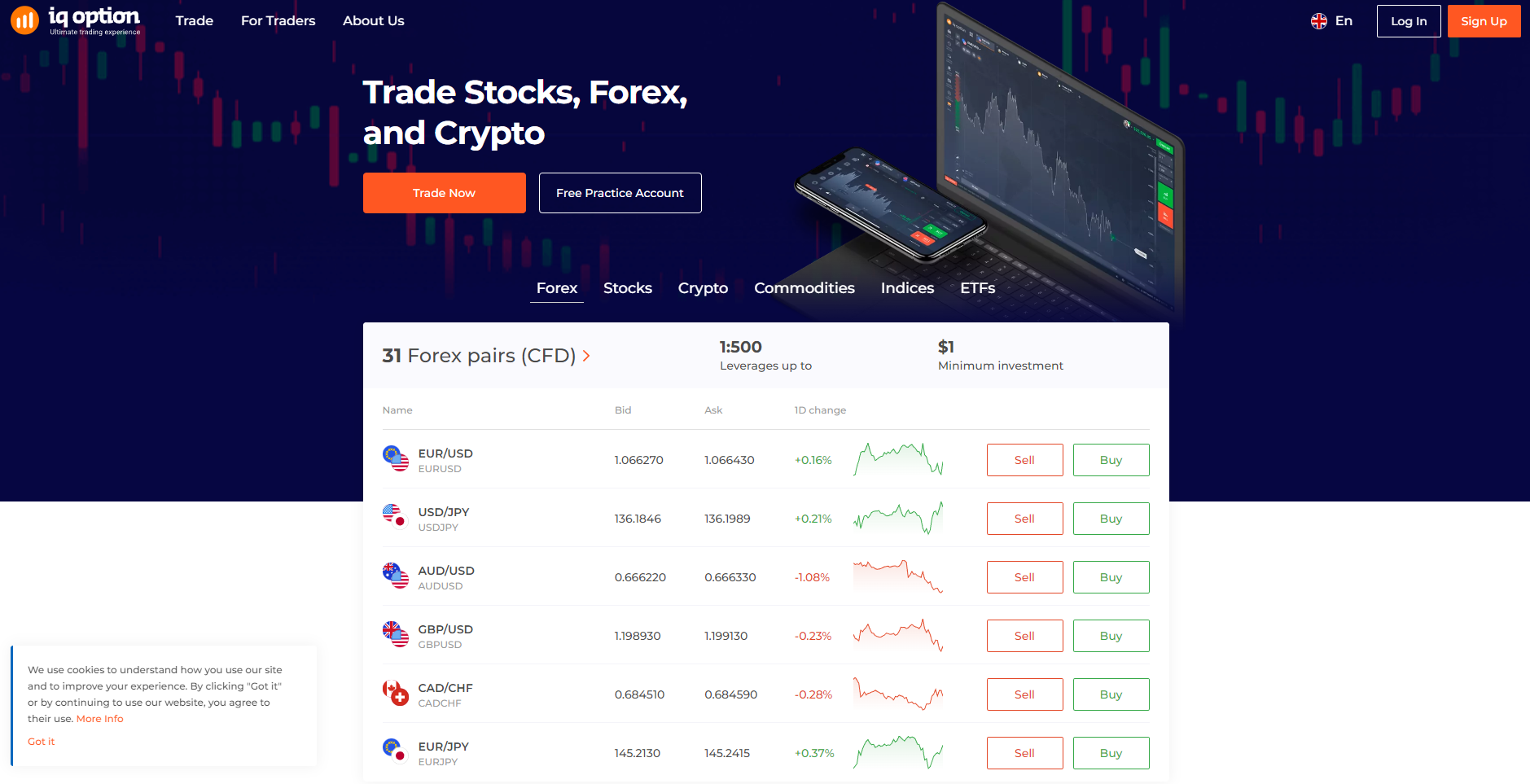
IQ Option é uma plataforma online para opções binárias. Ele apresenta um sistema de negociação exclusivo. A corretora fornece negociação Forex, CFDs, criptomoedas e outros serviços. A plataforma é acessível via computador e dispositivos móveis. O corretor era fundada em 2013.
Recursos
É um dos mais sistemas de corretores bem conhecidos. Alguns dos principais aspectos da plataforma são os seguintes:
- Você ganha um desconto de 50% em sua primeira depósito IQ Option com nenhum Taxas de câmbio IQ Option
- Existem mais de cem indicações técnicas
- Tutoriais benéficos
Aplicativo móvel
Ele oferece um aplicativo móvel para os sistemas operacionais Android e iOS. O aplicativo IQ Option pode ser baixado em iPhones, iPads ou smartphones Android. Assim, você pode negociar a qualquer momento e de qualquer local.
Com o aplicativo IQ Option, você pode assistir negociações ao vivo, monitorar suas transações ou configurar notificações personalizadas.
O aplicativo IQ Option já está disponível na App Store e nas lojas da Apple. Você pode simplesmente obtê-lo de lá.
Tipos de contas de negociação
IQ Option oferece três opções de conta:
- Conta de demonstração
- Conta ao vivo
- Conta VIP
Conta ao vivo
O pagamento mínimo na conta Live é $10. Tem um valor de negociação de limite inferior de US1. Isso permite que as contas padrão IQ Option sejam mais fáceis de usar para os recém-chegados.
Conta VIP
Para ter uma conta VIP em IQ Option, você deve fazer um depósito inicial de $1900 em dois dias. Com uma conta Premium, os usuários têm acesso a corretores de contas dedicados, 3% de ganhos extras e associação gratuita em competições de negociação IQ Option.
Além disso, Proprietários de contas VIP receba aulas personalizadas e mais recursos de treinamento comercial em comparação com usuários normais. Os registos VIP não são oferecidos a cidadãos da UE devido às limitações comerciais da ESMA.

- Retirada IQ Option tarifas: 0
- Comércio mínimo: $10
- Depósito mínimo: $10
- Bens: Forex, Ações, Criptomoedas, Commodities, Índices, ETFs
- Pontos de venda: IOS, Windows, Apple,
- Métodos de Pagamento: Cartões de crédito ou débito, transferências bancárias, Carteiras eletrônicas
- Depósitos com Visa: Disponível
- Saques com Visa: Disponível
- Taxas adicionais de visto: Não
(Aviso de risco: seu capital pode estar em risco)
#3 Pocket Option – Comece a negociar com um clique

O Pocket Option corretora é uma subsidiária da Gembell Limited, que foi criado por uma equipe de traders e investidores experientes. Por se basear em critérios amplos, a empresa oferece excelentes serviços aos opções binárias no mercado OTC acessível.
A empresa trabalha arduamente para tornar os procedimentos comerciais tão fáceis, diretos e eficientes quanto possível. Como resultado, Pocket Option criou um sistema comercial único para garantir negociação consistente para clientes profissionais.
Recursos
Esta plataforma inclui todos os recursos que um usuário deseja. Alguns aspectos importantes são os seguintes:
- Existem 150 instrumentos para trocar,
- Não há Depósito Pocket Option cobranças
- Sem retirada cargas em Pocket Option.
- Um sistema comercial vibrante e de ponta.
- Um 100% Bônus de opção de bolso no seu depósito inicial.
- Você pode simplesmente negociar por um valor tão baixo quanto $1.
Aplicativo móvel
Pocket Option permite aos usuários muita flexibilidade em termos de como, onde e o que eles escolhem negociar. Embora a interface principal do Pocket Option seja baseada na Internet, a negociação de desktop e smartphone também é oferecida. O aplicativo para smartphone é compatível com iPhones e telefones Android, tornando simples manter-se atualizado sobre as tendências econômicas. Pocket Options tem um aplicativo Android e IOS para MetaTrader 4 e MT5.

A corretora fornece uma base e aplicativo compatível com dispositivos móveis; oferece todos os recursos do sistema Pocket Option do site.
O programa está disponível gratuitamente e a IU é simples de instalar e usar. Se você tem a versão do iPhone 11.0 ou superior instalada, pode usar a versão do iOS. Se você estiver usando o Android, precisará ter a versão 4.4 ou superior.
Tipos de contas de negociação
A plataforma oferece aos seus clientes uma conta real negociar. , além de um Conta de demonstração do Pocket Option.
Conta Demo
Esta conta fornece a você $10.000 em moeda falsa para testar e melhorar suas habilidades comerciais. Você não precisa se inscrever com o Pocket Option para usar a conta demo. Para investidores iniciantes e experientes, começar com uma conta demo é um excelente ponto de partida.

Se você não tiver certeza sobre como negociar na conta real, você pode começar com o conta de demonstração; tem todos os mesmos recursos que a conta real.
Conta real
Para começar a negociar por dinheiro real usando o conta ao vivo, você deve fazer um pagamento inicial de $50. Depois de concluir seu pagamento inicial no Pocket Option, você também receberá mais 50% como bônus de boas-vindas. Você também terá a oportunidade de ganhar uma quantia adicional de dinheiro participando de um concurso quinzenal.
- Comércio mínimo: $1
- Retirada Pocket Option tarifas: Depende do método de retirada
- Valor mínimo do depósito: $50
- Bens: Mais de 100 ações, índices, criptomoedas, commodities e Forex
- Pontos de venda: versão desktop, aplicativo móvel Pocket Option, Android e Apple
- Métodos de Pagamento: Cartões de crédito ou débito, criptos, Carteiras eletrônicas, Skrill, Neteller, Web Money, Z Cash
- Depósitos com Visa: Disponível
- Saques com Visa: Disponível
- Taxas adicionais de visto: Não
(Aviso de risco: seu capital pode estar em risco)
Informações sobre a retirada com o método VISA
VISA é uma opção de saque para traders que usam Quotex, IQ Option ou Pocket Option. Você pode sacar fundos do site da sua corretora acessando a seção de retirada e selecionando Visa como sua opção de pagamento. Você será solicitado a fornecer os detalhes do seu VISA, como número, data de validade e CVV. Em alguns dias úteis após confirmar o valor do saque e enviar a solicitação, os fundos estarão disponíveis na conta da sua corretora ou no seu cartão VISA, dependendo se você está depositando ou sacando.
Cobranças e taxas de visto explicadas em detalhes

Na maioria dos casos, se você quiser transferir dinheiro de sua conta de corretor usando VISA, o processador de pagamento cobrará uma comissão. O corretor e o tipo de cartão VISA são dois fatores importantes que afetam esses custos. Este não é o caso com Quotex, IQ Option e Pocket Option. Aqui, todos os depósitos e saques com cartão VISA são gratuitos. No entanto, dependendo da sua localização, você pode estar sujeito a taxas de transações estrangeiras ao usar o VISA. Familiarize-se com a tabela de taxas com antecedência.
Métodos de pagamento alternativos ao Visa para comerciantes
Existem muitas ótimas alternativas ao Visa, incluindo:
- PayPal – é amplamente aceito e é conhecido por sua velocidade e conveniência.
- Payoneer – é um sistema de pagamento global. Payoneer oferece um Mastercard pré-pago para transações online e offline.
- Bitcoin – é uma moeda digital. As transações de Bitcoin são rápidas e seguras e oferecem baixas taxas de transação.
- Transferências Bancárias – são um método de pagamento tradicional. As transferências bancárias são seguras e confiáveis, mas podem ser lentas e caras.
Algumas outras alternativas são:
Como encontrar corretores de opções binárias que aceitam cartões Visa

Você vai aprender que a maioria das empresas de negociação de opções aceita pagamentos com cartão de crédito. A leitura das análises de cada corretora é provavelmente a melhor maneira de determinar se aquelas de seu interesse atendem a esse critério-chave. Você pode encontrar essas informações realizando uma pesquisa na web apropriada usando o nome da marca de sua corretora favorita.
A declaração da Visa de que permitirá o uso de seus cartões para transferência de fundos para contas de corretagem foi uma marco significativo que, sem dúvida, melhorou a reputação e a credibilidade da indústria de opções binárias. Como resultado desse grande desenvolvimento, a lista de empresas que permitem cartões de crédito e débito como um de seus métodos preferidos de transferência digital de fundos disparou.
Conclusão – Use Visa para negociar com esses melhores corretores de opções binárias!
Em resumo, listamos os 3 principais corretoras de opções binárias que aceitam Visa para depósitos e saques. Você pode depositar e sacar fundos com segurança e facilidade de sua conta de corretora usando um cartão de crédito ou débito Visa. Muitos investidores sofisticados usam cartões de débito Visa porque permitem transações rápidas.
Receba um bônus de depósito grátis de 50% em Quotex com nosso código promocional “boboker50“
As 3 melhores corretoras de opções binárias que aceitam Visa são essas, na respectiva ordem:
- Quotex – Nosso corretor Visa número um
- IQ Option – Taxas baixas e spreads brutos
- Pocket Option – Comece a negociar com um clique
(Aviso de risco: seu capital pode estar em risco)
Dúvidas frequentes sobre os corretores BO que aceitam VISA:
É seguro usar métodos de pagamento alternativos na negociação de opções binárias?
Sim, a maioria dos métodos de pagamento alternativos são seguros e oferecem proteção contra fraudes e transações não autorizadas. No entanto, lembre-se de que nem todos os métodos de pagamento são seguros. Recomendamos a escolha de provedores de pagamento confiáveis, como VISA, para obter a melhor experiência de negociação.
Os métodos de pagamento alternativos são melhores do que cartões de crédito ou VISA?
Depende de suas necessidades e preferências específicas. Os cartões de crédito podem oferecer programas de recompensas e vantagens, mas também podem gerar dívidas. Métodos de pagamento alternativos, como cartões pré-pagos e cheques eletrônicos, podem ser mais acessíveis para algumas pessoas.
Qual corretor de opções binárias aceita VISA?
Existem muitos deles. Neste artigo, discutimos todos os prós e contras do uso do VISA nas três plataformas:
Quotex
IQ Option
Pocket Option
Por que o VISA é preferido como método de pagamento na negociação de opções binárias?
O amplo alcance, rapidez e transações seguras do VISA o tornam a escolha preferida entre os comerciantes. Os corretores de opções binárias que oferecem suporte ao VISA oferecem um método fácil para os comerciantes depositarem e retirarem fundos. Sua aceitação mundial permite que os comerciantes gerenciem transações em vários corretores com facilidade.



