Торговля бинарными опционами – это способ покупки или продажи акций или любого актива путем спекуляции на их цене. Хотя трейдинг может показаться простым, на самом деле все не так просто.
Это потому, что, если движение цены актива не спекулируется правильно, трейдер потеряет всю вложенную сумму. Но точно предсказать движение цен на товары бинарных опционов немного сложно.

Смотрите мое видео с полной выкройкой:
Как трейдер, вы должны следить за тенденциями цен, колебаниями рынка и финансовыми новостями. Обладая соответствующей информацией, вы сможете сделать правильный выбор. Один из инструментов, который может помочь вам проанализировать рынок для получения прибыли, - это свечной график.
Хорошо знать:
- Свечные графики используются в торговле бинарными опционами для визуализации движения цен активов, показывая значения открытия, закрытия, максимума и минимума в течение определенного периода времени.
- Цвет и длина каждой свечи указывают на рыночные тенденции и настроения трейдеров: зеленый/белый указывает на рост цен, а красный/черный – на снижение.
- Распознавание свечных моделей, таких как бычьи, медвежьи и доджи, имеет решающее значение для прогнозирования движений рынка и принятия обоснованных торговых решений.
- Сочетание свечного анализа с другими индикаторами, такими как RSI и полосы Боллинджера, может улучшить торговые стратегии и повысить шансы на прибыльность торговли бинарными опционами.
Но что такое свечной график? Как можно читать свечной график? Каковы его образцы? Как сделать анализ диаграммы? Что ж, ответы на все эти и другие вопросы даны в этом руководстве.

Что такое свечной график?
Свечной график - это инструмент, который используют трейдеры при торговле бинарными опционами. Это простой способ лучше отобразить движение цены активов, торгуемых на рынке опционов.
С помощью свечного графика трейдер может быстро понять цену открытия, закрытия, максимальную и минимальную цену товара в данный момент времени. Поскольку этот график помогает трейдеру быстро понять движение цены, он стал надежным инструментом для торговли.
См. пример свечного графика:

В диаграмме, свечей несколько, каждая из них обозначает торговую сессию. Увидев отдельную свечу, трейдер может понять, какой будет цена актива в ближайшем будущем.
Анализ рынка свечных моделей более успешен и точен, чем любой другой график торговли бинарными опционами. Значит, этот метод обзора рынка действительно работает.
Кроме того, графики свечей помогают профессиональным трейдерам узнать основные настроения рынка. Таким образом, давая более глубокую информацию. Итак, понятно, почему трейдеры используют свечные графики.
Краткая история свечных графиков
Было бы здорово узнать происхождение свечного графика, чтобы лучше понять, как он начался.
Хорошо, Свечные графики не являются новой концепцией или методом анализа рынка. Это существует уже более десяти лет. Японский торговец рисом создал эту успешную торговую диаграмму еще в восемнадцатом веке, чтобы понять колебания цен на товар.

Мунехиса Хомма, создатель свечных графиков, понимал, что эмоции трейдеров играют важную роль в колебаниях цен на товары. Таким образом, он начал создавать свечные графики, и с тех пор они становятся популярными.
Этот график стал основой каждой торговой платформы и помог нескольким трейдерам получить более четкое представление о рынке.
Свечи против гистограмм
Свечные и гистограммы — оба способа представления торговых данных. Однако есть разница. По сравнению с гистограммами свечной график лучше, поскольку его легко понять.
Свеча представляет информацию с большим количеством цветов и визуальных эффектов. Это означает, что он лучше подчеркивает разницу в цене.
Различные компоненты свечи
Важно понимать компоненты свечи, чтобы читать ценовой тренд. товара на графике.
Свечной график состоит из двух разных элементов: тела и тени. Они бывают красного и зеленого цветов. Здесь тень представляет максимум и минимум сделки, тогда как тело указывает диапазон открытия и закрытия.
Даже крошечное изменение цвета тела или размера тени указывает на значительные колебания в мире торговли.

Цвет
В свече зеленого цвета, представленной белым, верхняя часть указывает цену закрытия актива, а нижняя часть - цену открытия.
Это означает, что рынок двинулся вверх, поскольку цена закрытия превышает цену открытия. Также, Если свеча зеленого цвета имеет длинный размер, это означает, что конкретный актив был куплен в большом количестве за определенный период времени.
С другой стороны, в свече красного цвета, также представленной черным цветом, нижняя часть указывает цену закрытия, а верхняя часть указывает цену открытия актива.
Итак, когда свеча красная, вы можете интерпретировать, что рынок движется вниз. Это потому, что цена открытия больше, чем цена закрытия. Длинная свеча красного цвета показывает, что данный товар был продан в определенное время.
Вкратце, цвет свечи на графике отображает движение цены элемента.
Тень

Как и цвет свечи, ее тень также указывает на изменение рынка. Поскольку многие трейдеры не могут проанализировать данные, представленные фитилем и хвостом свечи, они теряют свои деньги.
Если тень находится над телом свечи, ее называют фитилем. Однако, если тень находится внизу, это называется хвостом. Также, настроение торгового рынка можно интерпретировать по длине тени.
Верхняя и нижняя тень свечи почти никогда не бывают одинаковыми по размеру. Когда фитиль свечи длиннее ее хвоста, это показывает, что покупатели контролировали рынок в течение торговой сессии.
Точно так же, если хвост свечи длиннее фитиля, это означает, что продавцы на рынке были активны в течение торговой сессии. Независимо от положения обычно появляется длинная тень когда тенденция вот-вот закончится.
Но если фитиль и хвостик свечи одного размера, это указывает на нерешительность трейдеров и покупателей.
Что означают тело и тень свечи на графике?
Поскольку вы знаете, что означают тело и тень свечи, вот что означают их размер, соотношение и положение на графике.

Размер тела свечи
Если размер конкретной свечи на графике непрерывно увеличивается, ее цена также увеличивается. Но если длина свечи уменьшается, это говорит об обратном, т. Е. Цена товара на рынке упала.
Тело свечи к теневому рациону
По сравнению с тенью, если тело свечи длинное, цена товара на рынке движется вверх вместе с тенденцией. Если ситуация останется аналогичной и направление сохранится сильным, тело свечи будет продолжать расти.
С другой стороны, если тело свечи меньше тени, это означает, что цена товара не движется по тренду. Таким образом, на рынке присутствует неопределенность.
Положение тела
Помимо размера и соотношения свечей, положение тела также играет важную роль.
Например, если свеча небольшого размера, имеет длинный хвост и фитиль, это означает, что цена данного актива вернулась к своему первоначальному значению. Обычно это происходит, когда покупатели пытаются поднять цену, а продавцы ее снижают.
Следующая позиция - это когда подсвечник помещен на один конец и имеет длинную тень на другой стороне. Это происходит, когда цена актива изменилась в определенном направлении покупателями или продавцами.
(Предупреждение о рисках: ваш капитал может быть в опасности)
Психология свечей для торговли бинарными опционами

С помощью свечей вы можете прочитать психологию рынка при торговле бинарными опционами. По нашему опыту, лучший способ читать мысли других трейдеров – это интерпретировать фитили свечей. Смотрите картинку ниже:
Фитиль – один из лучших сигналов, если вы хотите знать, в каком направлении будет двигаться рынок. Многие люди торгуют свечами, а это означает, что перед фитилем другие трейдеры увидят полную свечу. На рынок приходят более сильные игроки и оттесняют рынок назад. Происходит отторжение, и в результате мы видим фитиль. Многие трейдеры сейчас оказались в ловушке неправильного направления, и им необходимо закрыть свои позиции.
Используя фитили в торговле бинарными опционами, мы можем добиться более высокого процента успешных сделок!
Смотрите мое видео об этом:
Как читать свечной график?
Трейдер может изучить цену актива на рынке, анализируя две части свечи, то есть тело и тень. Каждая свеча на графике представляет движение цены актива в определенный момент времени, например, за один день, одну неделю или один месяц.
Кроме того, каждый свечной график имеет четыре точки данных, то есть максимум, минимум, открытие и закрытие. Итак, если трейдер установил фиксированное время торговли, график обновится соответствующим образом.
Вы можете проанализировать тень и тело свечи, чтобы узнать настроение рынка. И, основываясь на своих предположениях, вы можете совершить сделку.
Объяснение различных моделей свечей:
Хотя существует несколько шаблонов, не все из них работают эффективно. Это означает, что они не помогут вам правильно прогнозировать рынок. И это может привести к потере значительной суммы денег.
Свечные модели делятся на две категории: бычьи и медвежьи. Основываясь на этих двух факторах, трейдеры могут понять различные закономерности.
Бычий паттерн
Когда на рынке доминируют покупатели, а не продавцы, формируется бычья модель. Это означает, что цена закрытия больше цены открытия. Зеленый или белый цвет означает наличие бычьего тренда на рынке.

Медвежий паттерн
Медвежий паттерн является противоположностью бычьего паттерна. Это означает, что продавцы контролируют рынок. Увидев медвежью модель, можно сделать вывод, что цена открытия выше цены закрытия. Также он представлен красным или черным цветом.
Вот несколько полезных медвежьих и бычьих моделей свечей, которые могут повысить прибыльность вашей торговли.
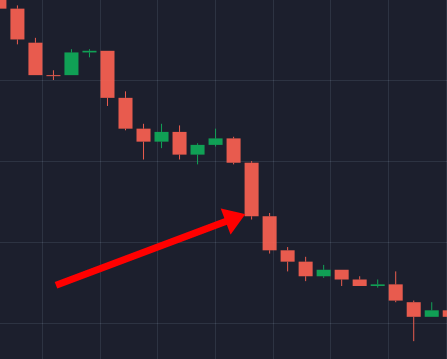
(Предупреждение о рисках: ваш капитал может быть в опасности)
Доджи Трейдинг
Когда бинарный рынок не контролируется ни медвежьим, ни бычьим, это показывает нерешительность рынка. Вот тогда и формируется паттерн доджи. Этот узор делится на четыре части.
Четыре различных шаблона доджи - это обычные доджи, доджи стрекозы, доджи надгробия и длинноногие доджи. Но не все они отражают нерешительность рынка. Трейдеры могут легко найти паттерн Доджи на свечном графике, потому что он представлен в форме креста.
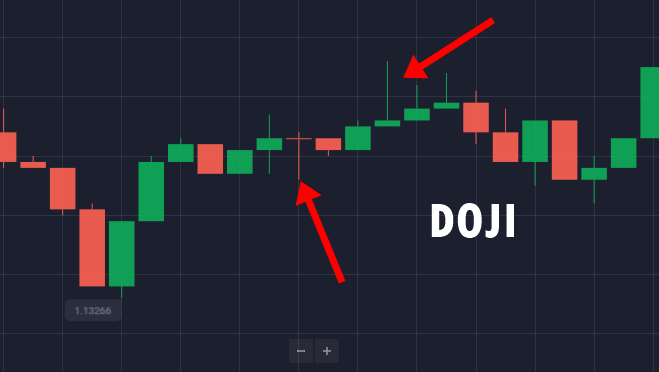
Преимущества метода Доджи
Если во время торговли рынок движется вверх и присутствует паттерн Доджи, вы можете сделать вывод, что действие продажи начинается, замедляя импульс покупки.
Если вы выйдете с рынка на основе анализа паттерна доджи, вы сможете получить значительную прибыль. Но важно подтвердить, что рынок показывает именно то, что показал паттерн Доджи. В противном случае вы можете столкнуться с огромными потерями.
Понимание различных вариантов свечей
Вот четыре популярных варианта паттерна доджи и их обозначение.

Стандартный доджи
Стандартный доджи на свечном графике означает, что цены покупки и продажи совпадают. Он представлен крестиком или знаком плюс.
Стрекоза Доджи
Стрекоза Доджи - это Т-образная свеча на графике. Сверху у него небольшое тело, за которым следует длинный фитиль внизу. Этот паттерн указывает на то, что рынок открылся по высокой цене и упал. Однако в конце сделки цена повысилась до того же уровня.
Короче говоря, стрекоза доджи образуется, когда цена снижается, но покупатели подтолкнули ее вверх в последнюю минуту.
Надгробие Доджи
Доджи надгробия - противоположность Доджи Стрекозы. Этот паттерн формируется, когда цена закрытия и открытия актива находится на одном и том же нижнем уровне.
Надгробный доджи показывает, что, когда рынок открылся, продавцы внезапно понизили его цену. Трейдеры могут получить хорошую прибыль, если будут торговать по фигуре доджи-надгробия.
Длинноногие доджи
Длинноногий доджи похож на обычный доджи. Однако у него сравнительно более длинные верхний и нижний фитиль. Длинный фитиль показывает нерешительность рынка.
Когда вы видите длинноногого Доджи, старайтесь не торговать бинарными опционами (вы должны знать, когда), так как это может привести к потере всех ваших вложенных денег. Как только фитиль укорачивается, вы можете торговать.
(Предупреждение о рисках: ваш капитал может быть в опасности)
Торговля на прорыве

Торговля на прорыве на свечном графике показывает движение цены актива. Цена товара либо вышла за пределы уровня сопротивления, либо выше уровня поддержки.
Уровень сопротивления или поддержки также можно рассматривать как точку стоп-лосса или уровень входа, который может помочь трейдерам получить огромную прибыль.
Когда цена выходит за пределы сопротивления или поддержки, у трейдеров есть два варианта. Во-первых, они могут уйти с рынка, если не хотят, чтобы цена вырвалась наружу. Уход с рынка может помочь этим трейдерам спастись от огромных убытков. Во-вторых, трейдеры, ожидающие прорыва, могут вскочить, когда он произойдет, и получить значительную прибыль.
После прорыва волатильность рынка увеличивается, и цена движется в сторону прорыва. Поскольку прорыв указывает на большее колебание цены и большую волатильность, он приносит большую прибыль.
Как работает торговля на прорыве
Чтобы торговать с использованием этого паттерна, вам необходимо проанализировать две вещи. Во-первых, постоянство касания уровня сопротивления. Если цена актива несколько раз коснулась уровня сопротивления и поддержки, их анализ становится более достоверным.
А во-вторых, как долго он остается в игре. Если уровень поддержки и сопротивления оставаться на своем месте надолго, исход более благоприятный.
Трейдеры могут быстро определить прорыв графического паттерна, поскольку он обычно находится в начальной точке тренда. Итак, если вы знаете, как определить прорыв на рынке, вы можете увеличить свою прибыльность.
Фальшивая торговля на прорыве
Следующая модель торговли свечами - это ложный прорыв. Этот паттерн противоположен прорыву, и это именно то, на что он похож.

Одна вещь, которая делает паттерн ложного прорыва интересным, — это его непредсказуемость. Цена движется таким образом, что трейдеры предполагают, что она может прорваться. Итак, они торгуют; однако цена обманывает трейдера, возвращаясь на тот же уровень.
Поддельный прорыв - одна из важных торговых моделей, которую могут понять и идентифицировать даже неопытные трейдеры. Ложный прорыв на торговом графике представляет собой одно из двух. Либо ценовая тенденция скоро возобновится, либо цена скоро изменится.
Такая ситуация возникает, когда трейдеры пытаются войти в рынок, когда все стабильно. Однако, когда они делают запись, цена обеспечить регресс. Таким образом, временные рамки имеют значение в ложном прорыве.
Как торговать на ложных пробоях?
Ложный прорыв может произойти при любых рыночных условиях и ценовом тренде. Успешно торговать на ложном прорыве, трейдерам необходимо сделать несколько вещей.
- Обратите внимание на финансовые новости.
- Постарайтесь понять причину ложного прорыва.
- Оценивает фальшивый прорыв и его влияние на ценовой тренд.
- Обратите внимание на крайние точки на рынке.
Если вы не хотите попасть в ложная торговля на прорыве, вы можете дождаться, когда цена актива закроется за пределами диапазона. Если это произойдет пару раз, можно предположить, что ценовой тренд начнется снова.
(Предупреждение о рисках: ваш капитал может быть в опасности)
Торговля по линии тренда
Линия тренда - это способ узнать тенденцию изменения цены актива на рынке. Определение линии тренда может помочь трейдерам совершать успешные сделки. Это потому, что линия тренда помогает трейдерам узнать, работает ли рынок в их пользу.
Линия тренда - это простой и легкий в использовании инструмент, разделенный на категории, т. Е. Нисходящая линия тренда и линия восходящего тренда.

Линия восходящего тренда на свечном графике указывает на избыточное количество покупок на рынке. Это означает, что цена актива, вероятно, возрастет. С другой стороны, нисходящая линия тренда указывает на давление предложения. Нисходящая линия тренда заставляет цену падать.
Кроме того, если линия тренда плоская, это означает, что рыночная цена движется в устойчивом направлении. Трейдерам не следует удерживать длинную позицию, когда они видят нисходящую линию тренда.
Линия тренда на графике создается путем соединения ряда цен. Чтобы получить лучшее представление, трейдеры должны сосредоточиться только на основных точках колебания. Построив линию тренда, вы сможете быстро определить рынок.
Вы должны торговать вокруг линии тренда, чтобы использовать лучшие торговые возможности и повысить прибыльность. Для входа в рынок нужно дождаться пробоя ценой линии тренда.
Бычья / медвежья модель поглощения

Другой популярный свечной паттерн - это бычий / медвежий паттерн поглощения. Это один из немногих шаблонов, который можно легко идентифицировать и который содержит всю важную информацию.
Паттерн бычьего поглощения на свечном графике показывает нисходящий тренд. Это означает, что на рынке наблюдается рост покупательной способности. Его представляют две зеленые свечи. Вторая зеленая свеча поглощает тело предыдущей красной свечи.
медвежий поглощающий узор является противоположностью модели бычьего поглощения. Этот паттерн возникает, когда цена актива падает по мере того, как на рынок выходит больше продавцов. Этот паттерн представлен двумя красными свечами, где красная свеча поглощает следующую зеленую свечу.
Когда вы замечаете медвежий или бычий паттерн, это означает, что будет разворот в тренде. Если трейдеры удерживают позицию по активу, ценовой тренд которого вот-вот закончится, они могут использовать эту модель для выхода из трендового рынка.
(Предупреждение о рисках: ваш капитал может быть в опасности)
Шаблон Утренняя Звезда / Вечерняя Звезда

В Утренняя звезда и модель вечерней звезды немного отличаются от моделей бычьего поглощения и медвежьего поглощения, поскольку они включают в себя три свечи, а не две.
Паттерн «Утренняя звезда» можно определить как визуальное представление трех свечей, образующих нисходящий тренд. Наличие утренней звезды на свечном графике указывает на разворот ценового тренда.
Паттерн "вечерняя звезда" на свечном графике - полная противоположность паттерну "утренняя звезда". Он представляет собой восходящий тренд на рынке. Паттерны «вечерняя звезда» также говорят о будущем развороте цены актива.
Эта модель обычно появляется, когда рынок показывает либо более высокие минимумы, либо более высокие максимумы. Если вы хотите торговать по свечному паттерну «Вечерняя звезда», не ждите, пока цены упадут, так как вы можете потерять сделку.
Образец пирсинга
Модель прокола формируется во время отката или в конце нисходящего тренда. Далее он делится на две категории: медвежью свечу и бычью свечу.
Этот паттерн можно найти на графике, когда вторая свеча, т. Е. Бычья свеча, закрывается на середине первой свечи, т. Е. Медвежьей. Такая ситуация возникает на рынке с нисходящим трендом.
(Предупреждение о рисках: ваш капитал может быть в опасности)
Проверенная свечная стратегия для начинающих
Я познакомлю вас с двумя проверенными свечными стратегиями для торговли бинарными опционами. Я часто использую их, когда понимаю, что рынок меняет направление.
Торговля на уровне поддержки и сопротивления
Первая стратегия, которую я люблю использовать в 60-секундных сделках с бинарными опционами. Я хочу проиллюстрировать это практической торговлей.
В этом примере я торгую EUR/USD. Во-первых, я установил таймфрейм на 60 секунд. Затем я переключаюсь между 60-секундным и 5-минутным графиками и внимательно смотрю на уровни поддержки и сопротивления и линии тренда. Эта стратегия направлена на предсказание следующей свечи для получения прибыли с помощью короткой 60-секундной сделки.
Для лучшего обзора я рисую уровни поддержки и сопротивления:

Данная стратегия предполагает торговлю в пределах диапазонов поддержки и сопротивления. Я предполагаю, что цена будет расти, но я еще не открываю сделку и жду подтверждающую свечу.

Как вы можете видеть на картинке выше, есть свеча-молот. Молот – хороший сигнал к тому, что рынок пойдет вверх.
Прежде чем начать торговлю, я сверяюсь с индикатором RSI и Полосы Боллинджера. Это необходимо сделать быстро, поскольку торговля носит краткосрочный характер. Оба торговых индикатора предполагают, что рынок совершит краткосрочное движение вверх. Поскольку существует свечной паттерн «молот», подтверждающий мое предположение, я открываю ордер на покупку.
Простая торговая стратегия, с помощью которой я заработал на этой сделке 955 евро из 500 евро. Стратегия проста, но эффективна, потому что у нас есть 3-кратное подтверждение того, что курсы будут работать, как предполагалось. Индикатор RSI, как индикатор моментума, помогает прогнозировать скорость и направление тренда.
Комбинируйте свечи с другими индикаторами
Последний способ торговли свечами — это комбинирование свечи с другими индикаторами. Делая это, вы максимизируете свои шансы на получение большей прибыли. Таким образом, вы не несете больше потерь. Таким образом, вы также открываете для себя множество различных торговых возможностей. И если вы выбрали правильное время, вы также можете открыть дверь к успеху и стать мастером-трейдером.

Как читать одну единственную свечу?
Если вы решите торговать отдельными свечами, вам нужно знать, как правильно читать одну свечу.
Когда вы торгуете одной свечой и замечаете длинную верхнюю тень, цена будет снижаться. Потому что инвесторы хотят продавать. С другой стороны, если вы наблюдаете длинную нисходящую тень, это означает, что рыночная цена растет.
Точно так же, если есть паттерн свечи Доджи, он показывает нерешительность. И эта штука указывает на одну и ту же цену открытия и закрытия. Наконец, если вы заметили на графике паттерн «молот» во время торговли одной свечой, это означает, что покупатели действуют.
(Предупреждение о рисках: ваш капитал может быть в опасности)
Вывод: используйте графические паттерны для выигрыша в бинарных опционах
Хотя для представления движения цены на рынке бинарных опционов можно использовать несколько графиков, лучше выбрать свечной график. Это потому, что это легко понять, и это говорит о полном настроении рынка.
Но чтобы получить прибыль, Очень важно выбрать свечной паттерн, который дает подробную информацию о ценовом тренде. Имея правильную информацию, вы сможете правильно спекулировать на рынке и совершить прибыльную сделку.
Чтобы стать успешным трейдером, вы можете выбрать правильный паттерн свечи, придерживаться детальной стратегии, и никогда не переставать учиться.
Для дальнейшего чтения вы также можете прочитать наш Руководство по шаблону ABCD для бинарных опционов или Руководство по гармоническим паттернам.
Часто задаваемые вопросы о свечных графиках:
Какова основная цель свечного графика в торговле бинарными опционами?
Свечной график используется для отображения движения цен активов при торговле бинарными опционами, помогая трейдерам быстро понять цены открытия, закрытия, максимума и минимума в течение определенного периода времени.
На что указывают цвета и длины свечей?
Цвет и длина свечей указывают на рыночные тенденции и настроения трейдеров. Зеленый или белый цвет означает рост цен, а красный или черный — снижение.
Каково значение тела и тени свечи?
Тело свечи представляет собой диапазон открытия и закрытия цены актива, а тень (или фитиль/хвост) указывает максимум и минимум сделки. Изменения их размера и цвета могут указывать на значительные колебания рынка.
Чем свечной график отличается от гистограммы?
Свечные графики предпочтительнее гистограмм, поскольку они представляют информацию более наглядно с помощью цветов, более эффективно выделяя разницу в ценах.
Каковы наиболее распространенные модели свечей в торговле бинарными опционами?
Общие свечные модели включают бычьи и медвежьи модели, модели Доджи (указывающие на нерешительность рынка) и конкретные формации, такие как Доджи Стрекоза и Доджи Надгробие, каждая из которых дает представление о рыночных тенденциях и потенциальных разворотах.
В чем важность сочетания свечного анализа с другими индикаторами?
Сочетание свечного анализа с другими индикаторами, такими как RSI и полосы Боллинджера, может улучшить торговые стратегии, повышая шансы на прибыль, предоставляя более полное представление о рыночных тенденциях и потенциальных движениях цен.








Enock Essandoh
говорит:я хочу узнать больше
Julie
говорит:Привет очень полезная информация
большое спасибо, только начал торговать бинарными опционами.